Contents
1. Virtualisation
There is lots information out there about virtualisation, this is just the cliffsnotes. For more: https://en.wikipedia.org/wiki/Virtualization
- Host machines run on physical hardware
- Host machines provide services to several virtualised guest machines
- They hypervisor tricks each guest into thinking it is running on dedicated hardware. The guest doesn’t know it’s a virtual machine.
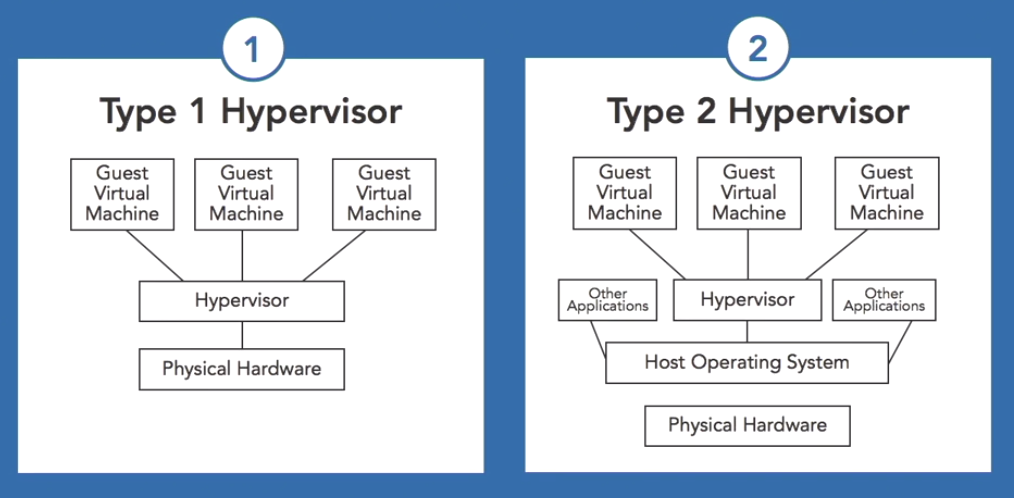
Types of Hypervisor
There are 2 types of hypervisor:
- Type 1 hypervisor: hypervisors run directly on the system hardware . EG: VMWare
- Type 2 hypervisor: hypervisors run on a host operating system that provides virtualization services, such as I/O device support and memory management. EG: Microsoft Hyper-V
Virtualisation Security
- Virtual machine isolation is critical. This means the guest cant interfere with the host or other VM’s
- Each server must have access to only its own memory and storage
- VM escape attacks attempt to break out of the guest environment
NB: Virtualisation platforms must be patched regularly against security vulnerabilities
VM Sprawl
As it is easy to create VM’s theses can lead to VM sprawl. This is where there are unused and unmaintained servers on the network. This is wasteful and also a security risk.
2. Cloud Computing Models
Cloud computing simply allows us to make hardware a complete abstraction, so that the engineers and developers, who manage servers and write code, don’t need to know the details of managing the underlying hardware platform. In many cases, that platform may be managed by a completely separate company. Cloud computing, simply defined, is the delivery of computing resources over a network, such as the internet, as a service.
Benefits of cloud computing:
- flexibility
- scalability
- agility
- cost effective
Cloud Computing Models
- Private Cloud: Organisations using the private cloud model want to gain the flexibility, scalability, agility and cost effectiveness of the cloud, but do not want to share computing resources with other organisations. In the private cloud approach the organisation builds its own cloud infrastructure or pays another company to do so.
- Public Cloud: The shared tenancy model. In this approach cloud providers build massive infrastructure in their data centres and then make those resources available to all comers. The same physical hardware may be running workloads for many different customers at the same time.
- Hybrid Cloud: This means the organisation uses both private and public cloud. They may use the public cloud for some computing loads, but they also operate their own private cloud for other workloads, often because of sensitivity concerns.
Public cloud uses a shared responsibility model. For example, if you purchase a cloud storage service, it’s your responsibility to know what data you’re sending to that service and probably to configure access control policies that say who may access your data. It’s the provider’s responsibility to encrypt data under their care and correctly implement your access control policies. See next section for more info on the shared responsibility model.
3. Public Cloud Tiers
There are 3 tiers of public cloud computing
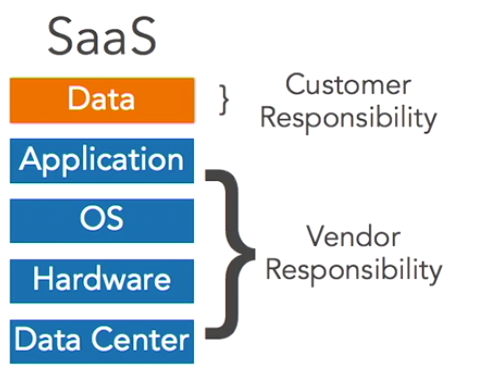
1. Software as a Service (SaaS)
In a Software as a Service model, the public cloud provider delivers an entire application to its customers. The customers don’t need to worry about processing, storage, networking, or any of the infrastructure details of that cloud service. The vendor writes the application, configures the servers, and basically gets everything running for customers who then simply use the service. Examples of this model are email delivered by Google apps or Microsoft Office 365, and storage services like DropBox.
2. Infrastructure as a Service (IaaS)
Customers of Infrastructure as a Service vendors purchase basic computing resources from vendors and piece them together to create customized IT solutions. For example, Infrastructure as a Service vendors might provide compute capacity, data storage, and other basic infrastructure building blocks. The three major vendors in the Infrastructure as a Service space are Amazon Web Services, Microsoft Azure, and Google Compute.
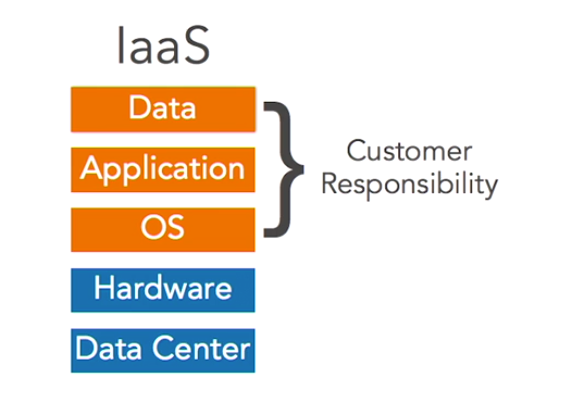
3. Platform as a Service
In this service vendors provide customers with a platform where they can run their own application code without worrying about server configuration. This is a middle ground between Infrastructure and Software as a Service. You don’t need to worry about managing servers, but you can still run your own code. The AWS Lambda Service is an example of PaaS.
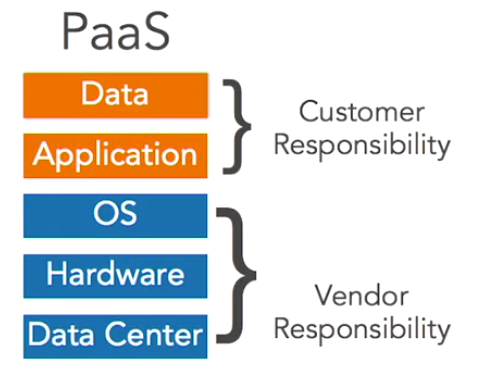
Summary of Key Differences
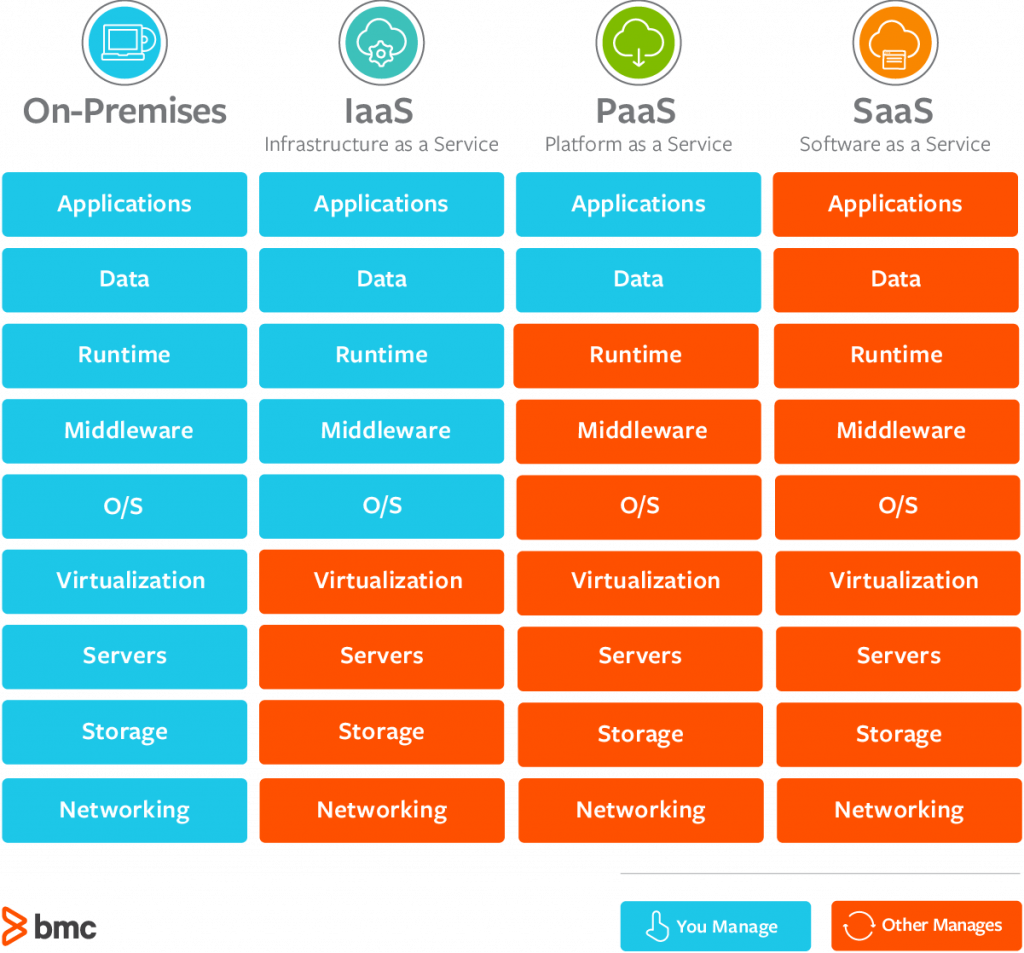
Image is from: https://www.bmc.com/blogs/saas-vs-paas-vs-iaas-whats-the-difference-and-how-to-choose/
4. Cloud Storage Security Issues
The basic principle that organisations should follow is that you should apply the same security controls to data stored in the cloud as you would data stored in your own data centre. If you’d encrypt information in your own data centre, you should encrypt it in the cloud. If you’d restrict access in your own data centre, you should restrict it in the cloud.
Cloud Storage Security Issues
- Encryption: The way you’ll implement encryption depends upon the type of service that you’re using, and the way that you use it. For example, when using an infrastructure as a service provider for servers, you may be able to encrypt entire virtual disk volumes to prevent everyone, including the provider, from accessing the contents of the disk.
- Access Control: You can often set access controls in the cloud the same way you would on a local file system. If you’re directly mounting the service as a drive, you can probably use the exact same access controls.
5. Security Service Providers
In some cases organisations turn to outside firms to provide critical security services. Vendors that provide security services for other organizations are known as Managed Security Service Providers, or MSSPs.
MSSP Service Examples
- Some manage the entire security infrastructure
- Some do a specific task should as manage system logs
- Some Manage firewalls or networks
- Some manage identity and access management
EXAM TIP: MSSPs may also be referred to as Security as a Service (SeCaaS)
Cloud Access Security Brokers (CASBs)
These add a third party security layer to the interactions that users have with other cloud services. They work in 2 different ways:
- Network Bases CASB: broker intercepts traffic between the user and the cloud service, monitoring for security issues. The broker can block request if it suspects an issue.
- API-Based CASB: The broker queries the cloud service via API. Broker may not be able to block requests depending on the API capabilities.
6. Desktop and Application Virtualisation
Organisations are increasingly looking at solution’s to help their employees work remotely. They need systems that allow employees to easily interact with enterprise systems from their homes or other locations.
Virtual Desktop Infrastructure
These solutions take the power of virtualisation technology and apply it to desktop computing. Users can use any system of their choice to access a standardised desktop environment that’s running on a remote server and has access to a standard set of applications and settings configured for enterprise use. These solutions might be a VDI product running in a company’s own data centre or a cloud based VDI product, such as Amazon’s WorkSpaces.
Application Virtualisation Technology
This allows users to access applications on their own systems that are actually running in different computing environment. This is also known as application streaming. Citrix XenApp, VMWare ThinApp and Microsoft App-V are all examples of application virtualization technologies.
Containerisation
This is another application Virtualisation approach. In this approach, multiple application containers run on the same instance of an operating system. The containerization platform such as the widely used docker, restricts the access that each application has to underline operating system resources.
The main benefits to this approach are that you don’t need to have a guest operating system running in the container and containers are portable across operating systems allowing them to be run on premises or in the cloud.
EXAM TIP: Comptia uses the term application cells to refer to containers.

For more on Containerisation: https://www.liquidweb.com/kb/virtualization-vs-containerization/