Contents
1. Managing Vendor Relationships
Security professionals must pay careful attention to managing these vendor relationships in a way that protects the confidentiality, integrity, and availability of their organisation’s information and IT systems.
This is known as Supply Chain Assessment.
Perhaps, the most important rule of thumb is that you should always ensure that vendors follow security policies and procedures that are at least as effective as you would apply in your own environment. Otherwise, vendors may become the weak link in the chain and jeopardise your security objectives.
Vendor Management Lifecycle
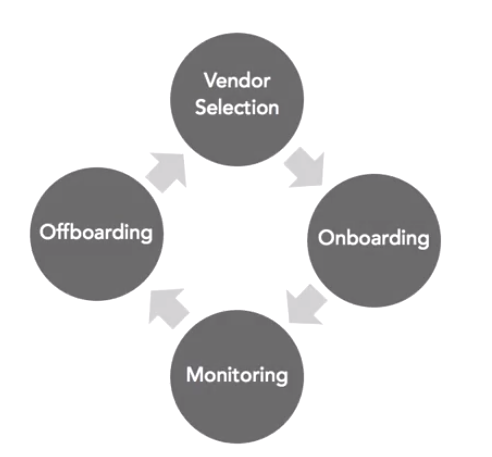
1. Vendor Selection
– May use a formal RFP or may be an informal process
– Should include security requirements
– Should evaluate security
2. Onboarding
– Verify contract details
– Arrange secure data transfer (check encryption etc…)
– Establish incident procedures
3. Monitoring
– Conduct site visits
– Review independent audits
– Handle security incidents (did they experience security issues? Did they report them?)
4. Offboarding
– Destroys confidential information
– Unwinds business relationship
2. Vendor Agreements
One of the most important components of managing vendor relationships is ensuring that appropriate agreements are in place to ensure interoperability and require that the vendor provide a level of service consistent with the customer’s expectations.
Service Level Requirements(SLRs)
SLRs that describe the organisation’s expectations of the vendor during the relationship. These requirements may address any concerns that the customer has for the quality of service provided by the vendor. For example, service-level requirements may include system response time, service availability, data preservation requirements, or any other parameters specified by the customer.
Service Level Agreement (SLA)
Once an organisation negotiates these SLRs with a vendor, it should document the results in a service-level agreement or SLA. The SLA is a written contract between the vendor and the customer that describes the conditions of service and penalties the vendor will incur for failure to maintain the agreed-upon service levels.
Other Agreement Types
- Memorandum of Understanding (MOU): this is simply a letter written to document aspects of the relationship. MOUs are commonly used when a legal dispute is unlikely but the customer and vendor still wish to document their relationship to avoid future misunderstandings. MOUs are commonly used in cases where an internal service provider is offering a service to a customer that is in a different business unit of the same company. This may also be known as memorandums of agreement or MOAs.
- Business Partner Agreement (BPA): these exist when two organisations agree to do business with each other in a partnership. For example, if two companies jointly develop and market a product, the BPA might specify each partner’s responsibilities and the division of profits.
- Interconnection security agreements (ISAs): these include details on the way that two organisations will interconnect their networks, systems and/or data. The ISA provides details on connection security parameters such as the encryption standards and transfer protocols that will be used.
Security and compliance Terms
- Document security and compliance requirements
- Facilitate customer monitoring of compliance
- Ensure the right of audit and assessment
3. Vendor Information Management
You must pay careful attention to the vendor’s information management practices. Data ownership issues often arise in supplier relationships. Particularly when the vendor is creating information on behalf of the customer. Agreements put in place prior to beginning a new vendor relationship should contain clear language around data ownership.
Data Ownership Provisions
- In most cases, a customer will want to ensure that the customer retains uninhibited ownership of the information
- Vendor’s right to use the information is carefully limited to activities performed on behalf of and with the knowledge and consent of the customer
- Vendor must delete information at the end of the contract
- Agreements should limit data sharing with third parties
- Agreements should include data protection provisions (backup procedures, fault tolerance etc…)