Contents
1. Understanding Data Security
Data States
1. Data at rest: is data stored somewhere for later use. This might be on a hard drive or USB stick, in a cloud service, or on a magnetic tape as part of a backup or archival solution. Data at rest is vulnerable to theft if an attacker gains either physical or logical access to the storage media.
2. Data in Motion: this is data that is moving around a network between two systems. It might be data moving from a storage location to a user’s computer, or data that is simply being transmitted between two systems, such as a user entering their credit card number into a website or sending an email message. Data in motion must be protected against eavesdropping attacks because this data often travels over public networks such as the internet.
Data Security Controls
- Clear policies and procedures covering data use and security
- Encryption to protect sensitive information. EG: file encryption to protect the data stored on a device, while transport layer security might protect information being exchanged between two systems over a network
- Access Control lists to control access to data
Big Data
Big data is the use of datasets that are much larger than those used by conventional data processing and analytic techniques. For example, big data rarely uses relational databases because of the significant overhead involved. Instead, big data storage and analysis uses specialised technology like the key value stores of NoSQL databases.
Big data storage and analysis introduces unique security concerns.
2. Data Security Policies
Data Security Policy Criteria
- Foundational authority doe data security efforts
- Clear expectations for data security responsibilities
- Guidance for requesting access to information
- Process for granting policy exceptions
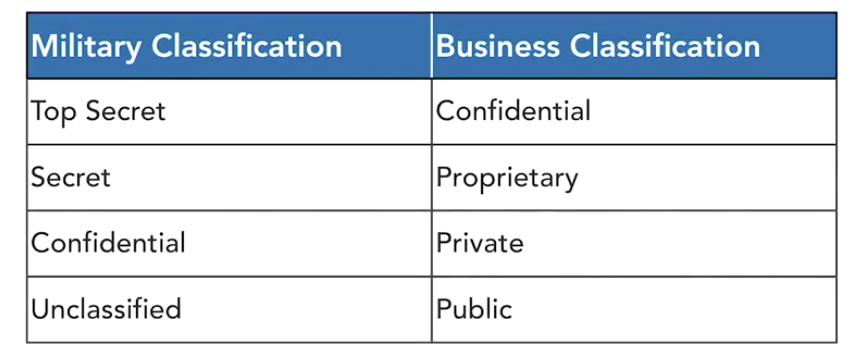
Data Classification Policies
These describe the security levels. Classification is used as the basis for other data handling requirements.
Data Storage Policies
- Appropriate storage locations. EG: no highly sensitive information is to be stored in the cloud
- Access control requirements including the process used to gain access to data
- Encryption requirements at different classification levels. EG: an organisation might allow the unencrypted storage of information on hard drives located inside a secure data centre, but require encryption for all other storage locations, such as cloud services or employee laptops.
Data Transmission Policies
Data is especially vulnerable when it is being transmitted over a network, because it becomes susceptible to eavesdropping attacks. Therefore, data transmission policies should cover
- What data may be transmitted over different kinds of networks, and under what authority
- Encryption requirements to protect information in transit over public or private networks
- Appropriate transmission locations for sensitive information, such as the types of information that may leave corporate networks without special permission
Data Lifecycle Policies
Describe end of life for data
1. Data Retention Policies: specify the minimum and/or maximum periods that an organisation will retain different data elements. EG: all tax records need to be kept for 7 years but customer credit card information should only be kept until transactions are complete.
2. Data Disposal Policies: describes proper techniques for destroying data that is no longer needed by the organisation. including the wiping techniques used to securely erase hard drives, flash drives, and other storage media before they are thrown away, recycled, or otherwise discarded. Simply deleting files or formatting a hard disc is not sufficient to remove all traces of that data from a device. Security administrators must use specialised tools to securely wipe storage devices, and prevent the future retrieval of information believed to be deleted.
3. Data Security Roles
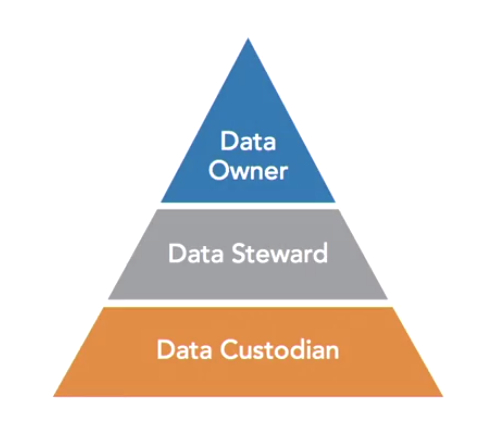
Data governance in many organisations follows a three tiered model of roles.
1. Data owner: a senior level official who bears overall responsibility for that data. The data owner sets policies and guidelines around data use and data security, and has the authority to make final decisions regarding a data set. most individuals who are senior enough to hold the position of data owner do not have the time available to get involved in the nitty gritty decisions of data governance. They usually delegate that responsibility to a Data Steward.
2. Data Steward: handles the implementation of the high level policies set by the data owner. In most cases, there is a reporting relationship between the data owner and the data steward.
3. Data custodians: actually store and process information and are often IT staff. They ensure that appropriate data protection measures are in place, including encryption, back ups, access controls, and other mechanisms that meet the confidentiality, integrity, and availability requirements set forth by data owners and data stewards.
Privacy Officers: These are responsible for ensuring that the organisation meets its privacy obligations.
4. Data Privacy
There are two classes of private information that should be carefully protected.
1. Personally Identifiable Information (PII): is a broad category of information that applies to any records that can be tied back to an individual person. PII might include extremely sensitive data such as credit reports and tax returns, or more mundane records such as movie viewing histories.
2. Protected Health Information (PHI): consists of medical records about individuals, collected by doctors, laboratories, hospitals, and other healthcare providers and clearing houses.
Generally Accepted Privacy Principles (GAPP)
These principles were developed through a collaboration between four major industry organisations.
1. Management: organisation handling private information should have policies, procedures, and governance structures in place to protect the privacy of that information.
2. Notice: Anyone who is the subject of records maintained by the organisation should receive notice of that fact, as well as access to the privacy policies and procedures followed by the organisation.
3. Choice and Consent: The organisation should inform data subjects of all of their options regarding the data that they own and obtain consent from those individuals for the collection storage, use, and sharing of their personal information.
4. Collection: The organisation should only collect personal information for purposes disclosed in their privacy notices.
5. Use, Retention, and Disposal: When the organisation collects personal information it should only use that information for the disclosed purposes. The organisation should dispose of the data securely as soon as it is no longer needed for the disclosed purpose.
6. Access: Organisations should provide data subjects with the ability to review and update their personal information.
7. Disclosure to Third Parties: The organisation should only share information with third parties if that sharing is consistent with the purposes disclosed in privacy notices and the organisation has the consent of the individual to share that information.
8. Security: The organisation must secure private information against any unauthorised access.
9. Data Quality: The organisation should take reasonable steps to ensure that the personal information they maintain is accurate, complete, and relevant.
10. Monitoring and Enforcement: The organisation should have a program in place to monitor compliance with its privacy policies and provide a dispute resolution mechanism.
5. Limiting Data Collection
Limiting data collection is the most important way that an organisation can protect personal privacy. If the organisation doesn’t collect personal information in the first place, it can’t abuse, lose, or otherwise mistreat that information.
Organisations should never collect information that falls outside of the disclosures that they’ve made to individuals. If you do have a legitimate need to collect more information that you’ve disclosed, you should revise your disclosures, notifying individuals of the new information that you’re collecting and how you will use it.
Minimise Information Collected: delete unneeded information quickly
You also have a responsibility to ensure that all of your data collection efforts use fair and lawful means of collection. The bottom line is that you should make all of your disclosures in plain language, make your data practices transparent, and avoid being dishonest or deceitful.
In some cases you may obtain personal information about individuals from third parties such as your business partners. In those cases you should take reasonable steps to ensure that the third party is collecting that information in accordance with privacy principles and that the third party has obtained prior permission to share it with you.
6. Privacy Assessments
Privacy Threshold Analysis (PTA)
These are used to determine whether a system contains or processes personally identifiable information in a manner that requires privacy control. The PTA requires that agencies answer a series of questions about the types of information that the system will handle, how the system is connected to other systems and other technical and operational details.
Privacy Impact Assessment (PIA)
When a system reaches the threshold specified in the PTA, organisations must complete a PIA that dives into deeper detail to ensure that the system meets privacy requirements. The PIA has 3 goals;
1. It ensures that the information system handles information in a manner that meets all applicable privacy requirements
2. It identifies the risks associated with handling personal information in the system.
3. it examines the controls in place to protect privacy and recommends remediation to mitigate privacy risks.
PIA Questions
Privacy Impact Assessments are governed by the E-Government Act of 2002 and must answer seven questions.
- What information is being collected?
- Why is the information being collected?
- What is the intended use of the information?
- With whom will the information be shared?
- What notice will be provided to individuals offering opportunities to decline providing information?
- How will the information be secured?
- Is the system subject to the Privacy Act?