1.5.1 Security Assessment Tools Vulnerability assessment tools come in 2 forms: Passive tools – monitor network traffic – observe system activity – provide reports but don’t interact with the systems (therefore no disruption to normal operation) Active tools – do interact with the systems to identify vulnerabilities and lack of security controls – does things like checking open ports or…
Author: sean
Security+ Course – 1.4 Application Attacks
1.4.1 Application Security Our increasing dependence on software makes it essential that we use software that is known to be secure and reliable. In one example of an application attack, a computer security expert hacked into a planes control system via the entertainment system by connecting his laptop to the device in his seat. He then used default username…
Security+ Course – 1.3 Understanding Attack Types
1.3.1 Denial of Service Attacks DoS Denial of Service attacks are a category of attack that disrupts the normal use of computing resources. they disrupt the availability of a web service by sending thousands or even millions of requests to a server, overwhelming it, and making it unable to answer any legitimate requests. These attacks can be difficult to distinguish…
Security+ Course: 1.2 Understanding Attackers
1.2.1 Cyber-security Adversaries Attackers come in different forms. Some of the ways they might differ are: internal vs external attackers Their level of sophistication Access to resources Motivation Intent Attackers range all the way from a a fairly unskilled lone wolf attacker, whose out for the thrill of breaking into systems, all the way up to secretive government agencies with…
Security+ Course – 1.1 Malware
1.1.1 Comparing viruses, worms and Trojans All malware has 2 parts: Propagation Mechanism- the way that a malware object spreads Payload- The malicious action that the malware performs Viruses These are spread by human behaviour The best way to fight viruses is with human behaviour training. Worms These spread by themselves They infect a system without a user doing anything…
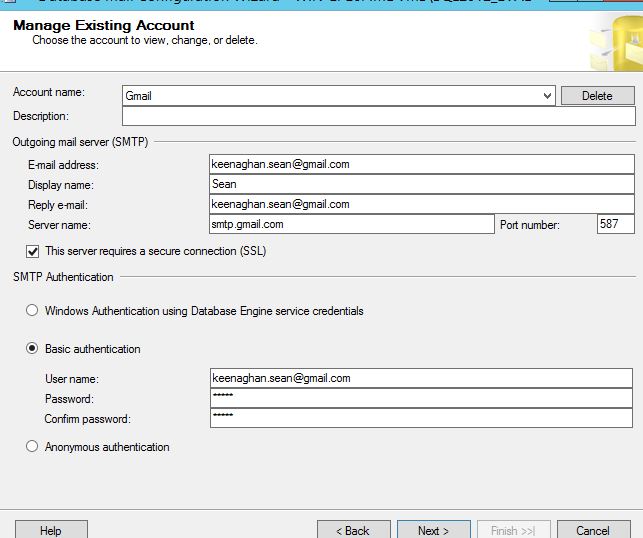
SQL Server: Configuring & Troubleshooting Database Mail
Database mail is great tool which allows you to send notification emails from your SQL Server. You can use to send notifications for things like backups, error, resource alerts etc… Configuring Database Mail Using the SSMS Wizard Go to Management -> Right Click on ‘Database Mail’ and select ‘Configure Database Mail’ Select the first option ‘Setup Database Mail by performing…