Contents
1. Security Controls
Security controls are procedures and mechanisms that an organisation puts in place to address security risks in some manner. This might include trying to reduce the likelihood of a risk materialising, trying to minimise the impact of a risk if it does occur, and trying to detect security issues that actually do take place.
Defense in Depth Principle
Multiple controls for one objective.
In this principle you apply multiple overlapping controls to achieve the same security objective. EG: when securing your home you might use both security alarms and CCTV cameras to detect intruders
Categorising Controls by Purpose
- Deterrent controls: discourage attack attempts. EG: barbed wire around a fence
- Detective controls: identify attack attempts and notify for the appropriate people. In the home security world this would be a burglar alarm. In the cybersecurity world this would be an IDS (Intrusion Detection System)
- Preventive controls: designed to stop attacks that are in progress. EG: locks on doors, IDS in cyber world
- Corrective controls: designed to help an organisation recover from an incident. EG: backups allowing you to rebuild after an incident.
Categorising Controls by Mechanism
- Technical controls: the use of technology to achieve security objectives. EG: firewalls, IDS, encryption, anti virus etc…
- Administrative controls: management processes we put in place to improve enterprise security. EG: user access reviews, log monitoring, background checks
- Physical controls: designed to deter, detect, or prevent unauthorised physical access to a facility. EG: fences, cameras, security guards, burglar alarms, and similar controls.
- Compensating Controls:These fill gaps when you are unable to implement other required controls. EG: you may have a policy in place to only use the latest versions of operating systems. But you might have a legacy system that has to work on an outdated OS. In this case you would use Compensating Controls.
Security Control Fails
- False Positive Errors: occur when a control inadvertently triggers when it should not. EG: when an AV system reports a security issue when none is present. These are dangerous because they reduce the confidence that security administrators have in the control, and sometimes lead to administrators ignoring future alerts from that system.
- False Negative Error: occurs when a control fails to trigger in a situation where it should. Returning to the examples of intrusion detection systems and anti-virus software, a false negative would occur if an actual security incident took place and the system failed to detect it, giving the administrator a false sense of security.
2. Security Policy Framework
Most security professionals recognise a framework consisting of four different types of documents: policies, standards, guidelines, and procedures.
Security Policies
- Provide the foundation for a security program
- Are written carefully over a long period of time
- Require compliance from all employees
- Are approved at the highest levels of the organisation
Writing good security policies
Don’t be too specific when writing the policies. EG: don’t write “Encrypt sensitive data with AES-256”. Or “Store employee records in room 226”. What if the encryption mechanism changes? Or the room you store the documents in changes? Then you have to re write the policies. It is best to write something like “Encrypt sensitive data in transit and at rest” or “Store employee records in HR approved locations”.
Security Standards
- Provide specific details of security controls: this is where you provide the specific details about protocols used etc…
- Derive their authority from policies
- Follow a less rigorous approval process
This site has a lot of information about security standards: https://www.cisecurity.org/
Security Guidelines
- Provides security advice to the organisation (EG: use a VPN when you are on an unencrypted network)
- Follow best practices from industry
- Suggest optional practices, not mandatory
Security Procedures
- Outline a step-by-step process for an activity. For example, the organisation might have standard operating procedures that cover a number of security topics, such as assigning user permissions, conducting account management reviews, or performing forensic analysis
- May require compliance depending on the organisation
EXAM TIP: be sure that you know the differences between policies, standards, guidelines, and procedures. Specifically, remember that compliance with policies and standards is always mandatory, complying with guidelines is always optional, and compliance with procedures can go either way, depending upon the organization and the specific procedure in question.
3. Security Policies
Every organisation has different approach to security policies.
Factors Affecting Security Policies
- Culture of the organisation: a laid back organisation may have fewer policies
- Industry: EG: healthcare providers will have greater controls around data privacy than other organisations
- Regulatory environment: organisations that process credit cards will have policies dictated by the Payment Card Industry Data Security Standard, PCIDDS
Common Policies
These are policies every organisation should have.
Security Information Policy
This should:
- clearly label who is responsible for security. Not the name of the individual, the position
- include descriptions of the roles that managers, employees, and other users play in information security
- see a requirement the organization follows security standards as well as the delegation of the authority to create those standards to an IT group or other entity
- describe the authority granted to individuals responding to a security incident
- include a process for handling violations and exceptions to the policy
Privacy Policy
Every organisation should have a published privacy policy. It should include:
- The type of personal information that you collect and store
- The purposes for which you collect, hold, use and disclose personal information
- How you collect and securely store personal information
- A promise not to ‘spam’, sell or rent a visitor’s email address
- How an individual may access and correct any information you hold on them, including unsubscribing from any email list
- How an individual may complain about a breach of the Australian Privacy Principles and how you’ll deal with the complaint
- Whether you disclose personal information to other people or organisations, and if they’re overseas which countries, and
Your contact details
Acceptable Use Policy (also known as Responsible Use Policy)
- Describes how individuals may use information systems
- Prohibits illegal activity
- Describes what personal use of computer resources is permitted
4. Risk Assessment
Risks are everywhere in the world of information security, from hackers and malware to lost devices and missing security patches, there’s a lot on the plate of information security professionals. Of course, addressing each one of these risks takes both time and money, therefore, information security professionals need to prioritise their risk lists in order to spend these precious resources where they will have the greatest security effect. That’s where risk assessment comes into play.
Risk assessment is the process of identifying and triaging the risks facing an organisation based upon the likelihood of their occurrence and the expected impact they will have on the organisation’s operations.
Key Terms
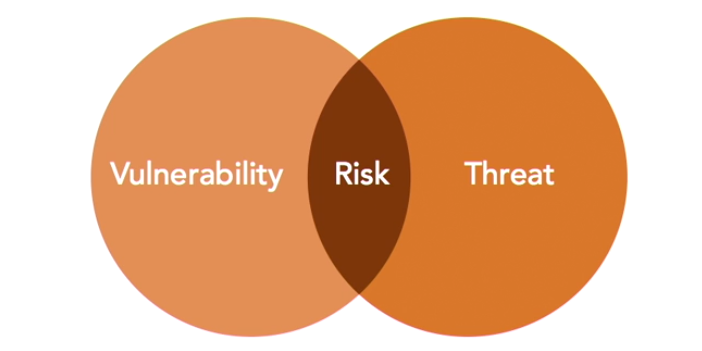
- Threats: external force jeopardising security. Threats might be naturally occurring, such as hurricanes and wildfires, or manmade, such as hacking and terrorism. You don’t have control over these
- Vulnerabilities: these are weaknesses in security controls. A Threat might exploit a vulnerability. These might include missing patches, promiscuous firewall rules, or other security misconfigurations. You do have control over the vulnerabilities in your environment
- Risks: This is the combination of a vulnerability and a corresponding threat. EG: if you haven’t update your antivirus signatures recently and hackers release a new virus on the internet, you face a risk. You are vulnerable because you’re missing a security control and there is a threat, the new virus.
Prioritising Risks
- Likelihood: Probability that a risk will occur. EG: there is a risk of earthquake in both California and Wisconsin. When you look at the data, however, you find that the probability of an earthquake occurring is far higher in California where almost 5,000 significant earthquakes occurred over the last 25 years. During that same time, Wisconsin didn’t experience a single major earthquake
- Impact: Amount of expected damage. EG: an earthquake might cause devastating damage to a data centre, while a rainstorm might not cause any damage at all.
Risk Assessments Types
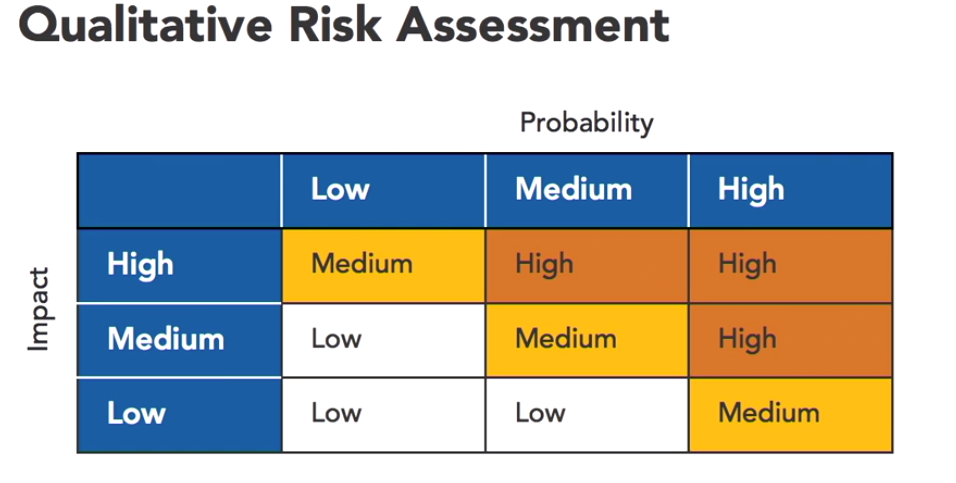
Qualitative Risk Assessment
This uses subjective ratings to evaluate risk likelihood and impact. It typically categorises them as low, medium, or high on both the likelihood and impact scales.
Quantitative Risk Assessment
The process of using numeric data to assist in risk decisions is known as quantitative risk assessment. Security professionals performing quantitative risk assessment do so for a single risk asset pairing.For example, they might conduct an assessment based upon the risk of flooding to a data centre facility. As they conduct this assessment, they must first determine the values for several variables.
Variable 1: Asset Value (AV)
The first of these variables is the asset value or AV. This is quite simply the estimated value in dollars of the asset. Risk assessors determining an asset’s value have several options at their disposal.
Original Cost Technique
The original cost technique simply looks at invoices from an asset purchase and uses the purchase prices to determine the asset value. This is the easiest technique to perform because it simply requires looking at invoices. However, it is often criticised because the costs to actually replace an asset maybe be significantly higher or lower if asset prices have changed since purchase.
Depreciated Cost Technique
The depreciated cost technique is an accounting favourite. It begins with the original cost and then reduces the value of an asset over time as it ages. The depreciation technique uses an estimate of the asset’s useful life and then gradually decreases the asset value until it reaches zero at the end of its projected lifespan.
Replacement Cost Technique
The replacement cost technique is the most popular among risk managers because it produces results that most closely approximate the actual costs that an organisation will incur if a risk materialises. The replacement cost technique goes out and looks at current supplier prices to determine the actual cost of replacing an asset in the current market and then uses that cost as the asset’s value. We might use this technique to value a data centre at $20 million because that is the amount of money that would be required to rebuild it after a disaster.
Variable 2: Exposure Factor (EF)
The exposure factor is based upon the specific risk considered in the analysis and it estimates the percentage of that asset that will damaged if a risk materialises. EG: if we expect a flood might damage 50% of our data centre, we’d set the exposure factor for that flood to 50%.
Variable 3: Single Loss Expectancy (SLE)
The next quantitative risk assessment variable is the single-loss expectancy or SLE. This is the actual damage we expect to occur if a risk materialises once. We compute the SLE by multiplying the asset value by the exposure factor. So, if we have a data centre valued at $20 million and expect that a flood would cause 50% damage to the facility, we compute our SLE by multiplying these two numbers together and finding that a single flood would cost $10 million in damage.
AV * EF = SLE
$20M * 50% = 50% $10M
Annualised Rate of Occurrence
A risk assessment must also consider the likelihood of a risk. That’s where the annualised rate of occurrence or ARO comes into play. The ARO is the number of times each year that we expect a risk to occur. In the case of a flood, we might consult FEMA flood maps and determine that there is a one percent annual risk of flood in the vicinity of our data centre. That’s the same as saying that we expect 0.01 floods to occur each year, so our AOR is 0.01.
Annualised Loss Expectancy (ALE)
Finally, a risk analysis should incorporate both of these likelihood and impact values. We do this by computing the annualised loss expectancy or ALE. This is the amount of money we expect to lose each year from that risk and it’s a good measure of the overall risk to the organisation. We compute the ALE by multiplying the single loss expectancy and the annualised rate of occurrence together. In the case of flood risk to our data centre, the SLE was $10 million and the ARO was 0.01.
Multiplying these together we get an annualised loss expectancy of $100,000. This means that we should expect to lose $100,000 each year from the risk of flooding to our data centre. It is important to remember that in reality this cost won’t occur each year. What will really have happened is $10 million in damage each time a flood occurs but since we expect that to happen only once every 100 years, it averages out to $100,000 a year.
SLE * ARO = ALE
$10M * 0.01 = $100,000
EXAM TIP: memorise these formulas and be prepared to work through a quantitative risk assessment calculation in the exam!
Time to Restore IT Services and Components
Quantitative techniques also help us assess our ability to restore IT services and components quickly in the event of a failure. We do this by looking at several time values. The values we use depend upon whether an asset is repairable or non-repairable. That is whether we can fix it or whether it needs to be replaced.
- Mean Time To Failure (MTTF): For non-repairable assets, those that we cannot fix, our most important metric is the mean time to failure or MTTF. This is the amount of time that we expect will pass before an asset fails
- Mean Time Between Failures (MTBF): This is quite similar to the MTTF. It’s simply the average amount of time that passes between failures of a repairable asset
- Mean Time To Repair (MTTR): This is the amount of time that an asset will be out of service for repair each time that it fails.
When we look at the MTTF, and MTTR values together, we can get a good idea of the expected downtime for an IT service or a component.
5. Risk Management
Once you complete a risk assessment for your organisation, you are left with a prioritised list of risks that require your attention.
Risk management is the process of systematically analysing potential responses to each risk and implementing strategies to control those risks appropriately.
Risk Management Strategies
- Risk Avoidance: When you avoid a risk, you change your organisation’s business practices so that you are no longer in a position where that risk can affect your business. EG: if the risk is flooding your data centre, you may move your data centre to an area that doesn’t have risk of floods
- Risk Transference: Shifts the impact of a risk to another organisation. The most common example of this is insurance. Many organisations are now also purchasing Cyber insurance to protect form hackers and identity theft. NB: you cant transfer all risk and no insurance will cover the loss of reputation
- Risk Mitigation: reduces the likelihood or impact of the risk. EG: in the risk of flooding example, you may get some specialists to install flood control measures that may divert flooding away from your data centre
- Risk Acceptance: you accept the risks without taking further action. This should take place only as part of a thoughtful analysis that determines the cost of performing another risk management action outweighs the benefit of controlling the risk
- Risk Deterrence: take actions that dissuade a threat from a exploiting a vulnerability. EG: deter the risk of burglary by using barb wire fences and guard dogs.
7. Risk Visibility and Reporting
Risk visibility and reporting techniques ensure that the results of these risk management processes are clearly documented and tracked over time. The core tool that most organisations use for maintaining ongoing visibility into risks is the risk register.
Risk Register
The risk register is a centralised document that tracks information about the nature and status of each risk facing the organisation. They typically contain the following information:
- Description of Risk
- Categorisation scheme to group risks
- Results of risk assessment containing probability and impact
- Risk rating
- Risk management actions
Risk Register Information Sources
- Risk assessment results
- Audit findings
- Team member input
- Threat intelligence from third parties