Contents
1. Brute Force Attacks
Brute-force attacks are the simplest form of attack against a cryptographic system. In a brute-force attack, the attacker simply guesses repeatedly at the encryption key until he or she stumbles upon the correct value for the key and gains access to the encrypted information.
Brute-force attacks can take a very long time to complete successfully, if they ever succeed. Brute-force attacks require very little information to wage. The attacker simply needs to have an example of encrypted ciphertext. For this reason, brute-force attacks are also called known ciphertext attacks.
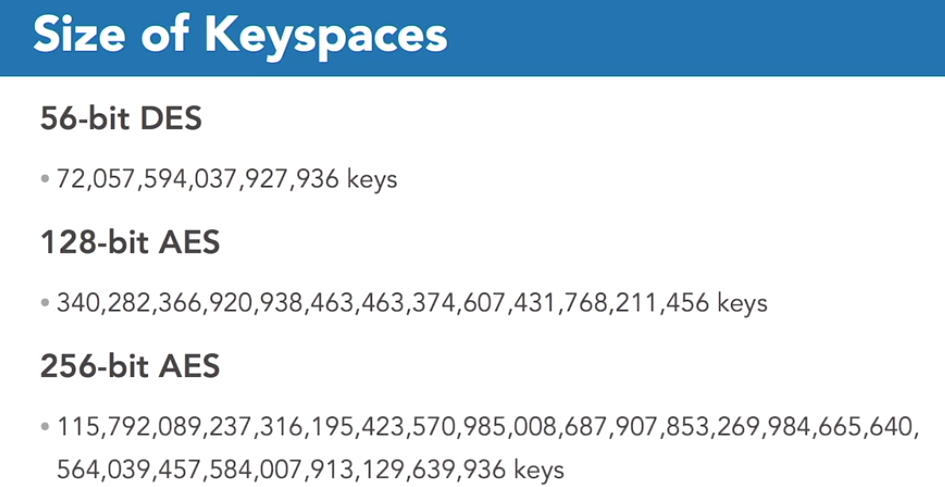
Modern cryptography algorithms are generally not susceptible to brute-force attacks due to the size of the keys. The diagram below shows the number of possible keys for different size encryption keys-
2. Knowledge based attacks
Knowledge-based attacks go beyond the simplicity of brute force attacks and combine other information available to the attacker with cryptanalytic techniques to break the security of encrypted data.
Frequency Analysis
In this attack, the person trying to break the code does statistical analysis of the cipher text to try to detect patterns. The analyst might use many of the common characteristics of the English language to help with this analysis.
For example, you may know that the most common letters in the English language are E, T, O, A, I, and N. If you suspect that a simple substitution cipher was used and see the letter X coming up repeatedly in the cipher text, there’s a good chance that X was substituted for E
EXAM TIP: you won’t need to know how to use these techniques on the exam. You just need to know that frequency analysis studies the patterns of letters in cipher text.
Known Plaintext Attack
If an attacker has access to both the encrypted and unencrypted versions of a message, they can perform what is known as Known Plaintext Attack.
Chosen Plaintext Attack
This is when the attacker has the ability to encrypt a message using the selected algorithm and key. The attacker can study the algorithm’s workings in greater detail and attempt to learn the way the algorithm works and how keys are being used.
