Contents
1.1.1 Comparing viruses, worms and Trojans
All malware has 2 parts:
- Propagation Mechanism- the way that a malware object spreads
- Payload- The malicious action that the malware performs
Viruses
- These are spread by human behaviour
- The best way to fight viruses is with human behaviour training.
Worms
- These spread by themselves
- They infect a system without a user doing anything
- Once a system is infected, they use this as a base to spread though the network
- The best way to avoid worms is by keeping software up to date and patched.
The RTM Worm
- Was the first major worm outbreak, in 1988
- Was written by Robert T. Morris
- Infected ~`0% of the internet
- Was an eye opening event for security
Trojan Horse
- Disguise themselves as beneficial programs
- Act as advertised when run
- Deliver their malicious payload behind the scenes
- Application control (whitelisting) provide good defence for Trojan horses
1.1.2 Comparing Adware, Spyware and Ransomware
Adware
This is malware with the specific purpose of displaying advertisements.
Adware mechanisms:
- Changing the default search engine
- Displaying pop up ads
- Replaces legitimate ads with other ads
Spyware
Spyware is malware that gathers information without the users knowledge or consent. It then report that information back to the author.
Spyware Techniques:
- Keystroke loggers
- Monitoring web browsing (reports back on user activity)
- Searching hard drives and cloud storage. This could search for confidential private information that can be used in identity theft
Ransomware
This blocks access to files/computer until a ransom is paid.
Ransomware Techniques:
- Arrives via email attachment
- Encrypts local files
- Demands ransom to release encryption key
1.1.3 Backdoors and Logic Bombs
Backdoor (Provides workaround access)
An example of this is when a programmer builds access in to the code that will allow them access the application in th future. This could be innocent enough, EG: they write something in the code to allow them remotely support the app, or they write it in a way to make it easier for a user to not have to enter credentials all the time. But this can fall into the wrong hands, especially if the information is in the user manual.
Backdoor Mechanisms:
- hardcoded accounts (specific usernames and accounts that always have access to the system)
- Default passwords (not changing them)
- Unknown access channels (ways to gain access without going through the normal channel)
In 2014, security experts found a backdoor in Samsung Galaxy devices that allowed remote access to data. Then in 2015, reports hot the media that default passwords in credit card readers allowed access to thousands of systems information.
You should routinely change default passwords and disable unused accounts
Logic Bombs
A logic bomb is malware that is set to execute its payload when certain conditions are met. This could be:
- a specific date and time
- the contents of a file containing specific information being accessed
- the results of an API call
A classic scenario for a Logic Bomb could be: A programmer creates a payroll system. This system has logic in it to see if this user is still active in the payroll. If the programmer disappears from the payroll, presumably terminated, the malicious code could execute in retaliation for the programmer being fired.
1.1.4 Advanced Malware
RootKits
The root account – super user account for admins with unrestricted access.
Originally, a rootkit was a type of malware designed for system privilege escalation. It is now used to describe software techniques designed to hide other software on a system.
RootKit Payloads:
- Backdoors
- Botnet Agents
- Spyware
User Mode RootKits
- run with normal user privileges
- Are easy to write and difficult to detect
Kernel Mode RootKits
- Run with system privileges
- Are difficult to write and easy to detect
Polymorphism
Most anti-malware software uses a technique known as signature detection. It recognises viruses by maintaining a database of known virus patterns, then compares suspect files to that database. Anti-Malware vendors must frequently update their databases. Polymorphic viruses fight signature detection by changing themselves constantly. Because of this the virus files look different on each system and the signatures don’t match, making it difficult to detect them.
Polymorphic Virus Techniques
- Changing their own code to avoid signature detection
- Using encryption with a different key on each infected system
Armoured Viruses
When viruses use polymorphism, anti-virus researchers have to pick them apart to retrofit anti-malware software to detect them properly. they do this using reverse engineering – they reach deep into the viruses code to see the virus’s DNA. Armoured Viruses implement techniques to defeat reverse engineering.
Armoured Viruses Techniques:
- writing the virus in obfuscated assembly language that hides the true intent of the code
- blocking the use of system debuggers
- preventing use of the sandboxing that can isolate the virus
1.1.5 Understanding Botnets
What are Botnets
One of the most common reasons hackers take control of systems is to steal their computing power, storage space, or network connectivity. They do this by joining infected systems to botnets. Basically, botnets are collections of zombie computers used for malicious purposes.
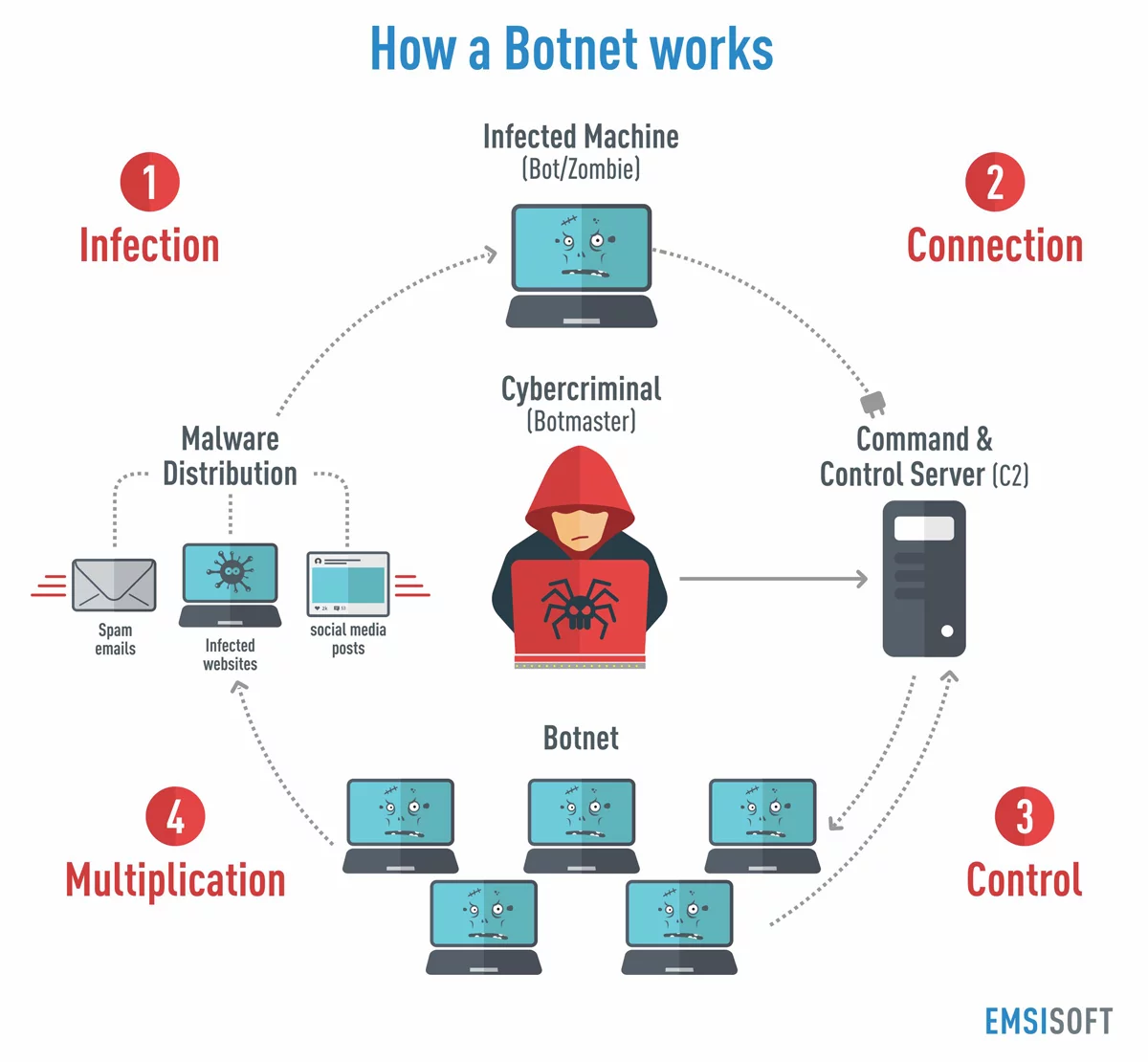
Steps of a botnet:
- Infect systems
- Convert to bots
- infoect others
- check with command centre
- get instructions
- Deliver payload (send spam, carry out DDoS attack etc…)
What are botnets used for:
- Renting out computer power
- Delivering spam
- Engaging in DDoS attacks
- Mining Bitcoin
- Waging Brute Force attacks
1.1.6 Advanced Persistent Threats
It is not always possible to protect yourself from all vulnerabilities as not all vulnerabilities are known.
Modern operating systems contain literally millions of lines of code. There is no doubt that in all that code there is a vulnerability that the security community hasn’t found yet. When a security researcher finds a vulnerability they general handle it in an ethical and responsible fashion, this means they notify the vendor responsible for the vulnerability and give them the opportunity to fix it before disclosing the vulnerability.
Zero-Day Vulnerability
This is a vulnerability in a product that has been discovered by at least one researcher but has not yet been patched by the vendor.
Window of Vulnerability
The time between the discovery of a zero day vulnerability and the release of a security update.
Advanced Persistent Threats (APTs)
- Are well funded and highly skilled (professionals, crime gangs etc…)
- are typically government sponsored (military)
- have access to zero days and other sophisticated weapons
- work methodically to gain access to a target
Defending Against APTs
This is difficult as most organisations don’thave the resources that APTs have, but there are some steps you can take:
- build a strong security foundation (patching etc…)
- Implement strong encryption
- use rigorous monitoring
