Contents
1.5.1 Security Assessment Tools
Vulnerability assessment tools come in 2 forms:
- Passive tools
– monitor network traffic
– observe system activity
– provide reports but don’t interact with the systems (therefore no disruption to normal operation) - Active tools
– do interact with the systems to identify vulnerabilities and lack of security controls
– does things like checking open ports or checking exploits against known vulnerabilities
– can disrupt normal operation (but if they can, maybe attackers can too…)
Vulnerability tools may also be used for configuration compliance scanning. They can scan a system and retrieve its configuration, then compare this config against a standard security configuration.
Honeypot’s
These are decoys that are used to take the attackers attention from the legitimate servers. This is a passive tool that sits on the network and is designed to look appealing to hackers. It may have some known vulnerabilities that might show up when scanned. Or could have a name like “Credit Card Server”.
The Honeypot server has no other service so no one should be accessing it. This means that anytime someone does access it, its more than likely an attacker. This activity is reported to security administrators and carefully monitored.
Honeynet’s
These are a variation of honeypots. It is a network setup with known vulnerabilities to purposefully invite attackers. They are then monitored and their methods are studied to be used in increasing security. This can also be known as a Dark Net as they remain unused or are in the dark.
Protocol Analysers (EG: Wireshark)
These allow you to peer into the contents of network traffic. This can be used when diagnosing a network problem or security incident. There are some privacy concerns with these as it allows you to look into the activity of different users on the network.
1.5.2 Scanning for Vulnerabilities
There are major types of vulnerability scanners:
- Port scanners: which probe a system for open network ports
– scanning ports is a bit like checking door handles to find an open door. The scanner probes the system for open network ports
– it checks all of the possible 65,535 ports to see which ones are open
– NMAP is one of the most popular port scanners
– you should close any of the ports you don’t need to be open - Vulnerability scanners: which scan those open ports for known vulnerabilities
– they have a database of known vulnerabilities which they test against the open port
– the results of these scans can be very useful for security administrators, but in the wrong hands, this information can be very dangerous!
– Nessus is one of the most popular scanning tools. Its a web based tool. It returns a lot of information about certificates, version of IIS, RDP login screen shots etc… - Application scanners: these do deep scans of web applications to detect flaws
1.5.3 Assessing Threats
Terminology
Threat: this is an external force that jeopardises the security of your information and systems. This could be naturally occurring (earthquakes, bush-fires etc…), or man made (hacking or terrorism). Normally you can’t control what threats are out there.
Vulnerabilities: these are weaknesses in your security controls that a threat might exploit. These might include missing patches, promiscuous firewall rules, weak passwords etc…
Risk: Vulnerability + Threat = Risk. This occurs when you have both a vulnerability and a corresponding threat looking to exploit that vulnerability.
Security professionals use likelihood and impact information to help prioritise the many risks facing an organisation. EG: Security Professionals in California need to be vigilant about earthquakes and their devastating effect, where as someone living in Wisconsin doesn’t have to be as concerned about earthquakes.
1.5.4 Threat Assessment Techniques
Baseline Reporting
This provides an initial review of the systems security status. It compares the security configuration against the organisations security configuration standard to find any differences or gaps. There are tools to help with this process.
Organisations using the CIS (Center for Internet Security) configuration baseline tool may use the Center’s configuration assessment tool, a Java based utility that compares a systems current configuration to a s security baseline.
Attack Surface Reviews
These reviews find the “attack surface” of a system. This means they find all possible means of attacking a system. These reviews use port scanners, vulnerability scanners, vulnerability scanners and application scanners. You adopt the mindset of an attacker and try to find ways to exploit the system.
Code Reviews
These are critical when an organisation is involved in the creation of custom code. These reviews perform assessments of software security. This includes peer code reviews for an extra set of eyes to detect security issues.
Architecture Reviews
IT systems are complex and are made up of many different resources, including: databases, networks, storage etc… How this resources fit together can sometime create security vulnerabilities. Architecture reviews take a look at the whole IT system from a high level analysing how components interact with each other.
1.5.5 Penetration Testing
Executing an attack on the system is the best way to understand its vulnerabilities. This is what penetration testing does.
Testers actually attack systems and networks. They verify that threats exist and exploit the vulnerabilities. They also test security controls by attempting to bypass or defeat them.
Penetration tests loop back and forth between the discovery phase and the attack phase.
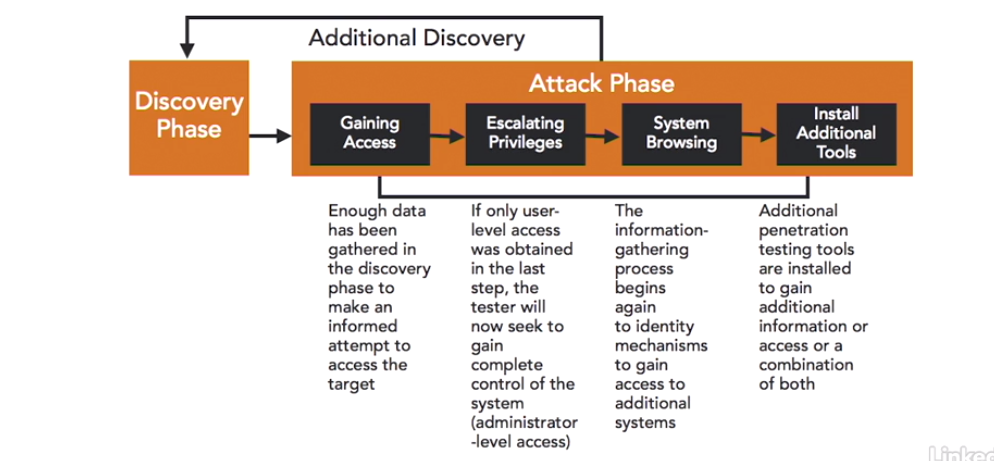
Types of Penetration Tests
- White Box: attackers have full knowledge of the network environment. This is simulating an insider attack.
- Black Box: attackers have no knowledge of the network environment. This is simulating an external attack.
- Grey Box: attackers have some knowledge of the network environment. This type of test commonly used as it combines some of the external perspective of the Black Box test with the time saving nature of the White Box test.
Concepts of Penetration Testing
- Pivot:attackers gain access to a less secure/more vulnerable system on the network, then leverage this or use it as a base to gain access to more secure systems.
- Persistence: After exploiting a vulnerability the attacker installs some tools which allow them to gain access to the system at a later stage, like a backdoor. Even if the administrator fixes the original vulnerability the attacker has another method of accessing the system.
1.5.6 Advanced Vulnerability Scanning
Non Intrusive Scanning (Safe Mode)
This will not disrupt the system operations as it does not perform actual attacks on the system. This can be useful if you do not want to disrupt production servers. But it doesn’t give an accurate picture of security because it fails to show if those attacks would have been successful.
Intrusive Scanning (Dangerous Mode)
This performs actual attacks on the system and disrupts it. It is best not run on production servers. You can run it on clones of the production servers.
Scanning Errors
False Positive: this is when a scan reports a vulnerability that does not exist.This requires verification by security administrators. The problem with False positive errors is that people may become desensitised by them if they happen frequently.
False Negatives: These are far more dangerous. This occur when a scan fails to report a vulnerability that does actually exist. This may be due to a misconfiguration of the scanner or it might simply be a vulnerability that the scanner doesn’t know about yet.

