Contents
1.3.1 Denial of Service Attacks
DoS
Denial of Service attacks are a category of attack that disrupts the normal use of computing resources. they disrupt the availability of a web service by sending thousands or even millions of requests to a server, overwhelming it, and making it unable to answer any legitimate requests. These attacks can be difficult to distinguish from legitimate requests made to the server.
Limitations of a DoS attack:
- Sending lots of requests that tie up the server requires a large network connection
- Once the victim recognises they are under attack, they can simply block the IP addresses of the attackers
DDoS (Distributed Denial of Service)
DDoS attacks use botnets to overwhelm the target. The attacker uses large numbers of computers and huge volumes of traffic to overwhelm a server or network, slowing to or rendering it completely unresponsive. The attackers can use thousands of computers owned by unsuspecting customers all over the world which they use to create their network with these “zombie computers”. this network is the used to focus traffic, such as a simple web page request, on their target. The target can will then often get bogged down or stop responding completely.
Smurf Attack
I found a lot of good info on this on: https://www.imperva.com/learn/application-security/smurf-attack-ddos/
This is a DDoS named after the DDoS. Smurf malware that enables it execution. This attack uses the reply of an ICMP echo request to flood the target. In an IP broadcast network, a ping is sent to every host, and every host will send a response. The Smurf attack abuses this functionality. The steps are:
- Smurf malware is used to generate a fake echo request containing a spoof source IP, which is the IP of the target server
- The request is sent to an intermediate IP broadcast network
- The request is transmitted to all of the network hosts on the network
- Each hosts responds with an ICMP response to the spoofed source address (the target)
- With enough of these responses the target can get flooded and the server is brought down
The amplification factor of the Smurf attack correlates to the number of the hosts on the intermediate network.
Defending against Smurf Attacks:
- Disable IP directed broadcasts on your router
- Set the operating system to disallow ICMP responses to IP broadcast requests
- Configure the perimeter firewall to disallow pings originating from outside your network
Amplification Attack
https://www.imperva.com/learn/application-security/dns-amplification/
In this attack the attacker exploits vulnerabilities in DNS servers to turn initially small queries into much larger payloads, which are used to take down the target servers. DNS amplification is a type of reflection attack, which uses publicly accessible DNS severs, and elicits a response from theses DNS revolvers to flood the target with large quantities of UDP packets.
During a DNS amplification attack the attacker sends a DNS query from a spoofed IP address (the victims) to open DNS revolvers, which in turn reply to the spoofed IP address with a DNS response. With numerous fake queries and several DNS revolvers replying, the victims network can easily become overwhelmed with the responses.
Amplification Factor
The degree to which the attack increases in size:
Reply/Request = Amplification
512 bytes/64 bytes = 8x Amplification
1.3.2 Eavesdropping Attacks
This is when an attacker gets physical or logical access to the network and they can eavesdrop on the communication between systems. They can then potentially decrypt encrypted communications without the senders knowledge. Some ways they can do this is by using ARP or DNS poisoning attacks to trick a system into sending traffic directly to the attacker rather than the intended recipient.
Man in the middle attack
Encryption such as HTTPS stops intermediate devices from viewing or altering the communication, but a Man In The Middle Attack can get around this. They trick the victim into connecting to the attackers server instead of the legitimate server they were trying to connect to (they could use DNS or ARP poisoning – see section 3.3). The victim then authenticates with the fake server. The attacker then connects to the legitimate server and acts a relay between victim and legitimate server. They attacker can view the communication between victim and legitimate server. The attacker receives the requests from the user, passes them onto the server, and receives the real responses, reads them, and then replays them to the original user, who has no idea that there is a man in the middle intercepting those communications.
Man in the browser attack
https://www.owasp.org/index.php/Man-in-the-browser_attack
This is where the attacker compromises the users web browser or a browser plugin to gain access to web communications. A Trojan Horse is used to intercept and manipulate calls between the browser and its security mechanisms. This Trojan Horse sniffs or modifies transactions as they are performed, but still displays back the users intended transaction. It is hard for the victim to suspect any foul play as everything appears to be working as normal.
Replay Attack
If attackers have the ability to capture network traffic, they can also conduct a Replay Attack. A Replay Attack uses previously captured data, such as an encrypted authentication token, to create a separate connection to the server that is authenticated. In a Replay Attack, the attacker typically cannot see the actual credentials, but only has the encoded version of them available. Replay Attacks are easily defeated by using a simple session token, or through the use of timestamps. Each session established with a remote system should use a new token that is chosen randomly and has a limited lifespan suitable to the length of time the authenticated session should last.
Encryption, secure network configuration, and strong authentication mechanisms are all good ways to protect your applications and users from falling victim to eavesdropping attacks.
1.3.3 Network Attacks
Packets are the basic unit of network communication. Each time you request a web page, send an email or transfer other information over the network, its divided up into small packets of information that are then reassembled at the receiving system.
Packets carry a data payload but must also include header information. The header is like the envelope that carries the data. It has information like the source and destination addresses, and flags. These flags are single bit fields that are either a one or a zero. If a flag field is set to one it indicates a special purpose packet. Some of the more commonly used flags are:
- SYN – the Synchronisation flag is the first step in establishing a 3-way handshake between 2 hosts
- ACK – the Acknowledgement flag is used to acknowledge the successful receipt of a packet
- FIN – the Finished flag means there is no more data coming from the sender
For more on Flags have a look at: https://www.keycdn.com/support/tcp-flags
Christmas Tree Attack
This is when all the flags in the packet are set to one (apparently its lit up like a Christmas tree…). Having all the flags set can increase the processing on the target and may either slow it down, or eventually crash the system. Its a type of Denial of Service attack.
The Christmas Tree Attack can also be used to identify which operating system the target victim is using.They can work this out by the response of the system receiving the Christmas Tree packet.
Christmas Tree packets have no legitimate use and can therefore be filtered out by Intrusion Detection Systems or advanced firewalls.
DNS Poisoning
Domain Name System is like a phone book for networks that has a record of computer/domain names and the IP addresses relating to them.
DNS Poisoning, also known as DNS Spoofing, disrupts the normal operation of DNS by providing incorrect DNS query results to the victim. Instead of sending the victim to the legitimate server it requested, the attacker sends them to their illegitimate server. EG: a user tries to go to their bank website, but they get directed to the attackers fake bank website, the victim then enters their details and the attacker captures them.
Attackers achieve DNS poisoning by poisoning the DNS cache on the victims DNS server. They do this by pretending to be an authoritative Name Server.
DNS Cache Poisoning Process:
Poisoned DNS Cache:
The above images are from: https://www.cloudflare.com/learning/dns/dns-cache-poisoning/
Preventing Against DNS Poisoning
Standard DNS doesnt use any verification which leaves it vulnerable to attacks. DNSSEC (Domain Name System Security Extensions) uses public key cryptography as a means of verifying DNS data which would help against DNS Poisoning. But it is not yet widely used.
ARP Poisoning
ARP (Address Resolution Protocol) translates IP addresses to the hardware(MAC) addresses used on local area networks. ARP poisoning is a spoofing attack that provides false information in response to ARP requests. Unlike DNS Poisoning, ARP poisoning only works on local area networks. In an ARP poisoning attack the attacker could pretend to be the victims network gateway, and the victim would send its traffic to it. The attacker could use this as a “Man in the middle” attack.
Typosquatting or URL Hijacking
This is where attackers register domain names on hundreds of variations of official sites. EG:, “Gooogle.com” instead of “Google.com”. If a user incorrectly spells the domain name they are sent to the attackers malicious site.
Domain Hijacking
This is when an attacker tries to illegitimately transfer ownership of a domain to themselves. Or they may conduct a DNS attack that changes the legitimate sites records.
1.3.4 Network Address Spoofing
Network addresses are easily altered by anyone with administrative access to a system so they should not be relied upon for authentication purposes. Attackers can modify both the IP address and the MAC address of a system.
MAC Address Spoofing
MAC addresses are easily altered by an administrator. There are many software tools that allow you change the MAC address on the driver. On an Apple Mac it is as easy as running the command: sudo ifconfig en0 ether 00:00:aa:55:66:cc:ff
IP Address Spoofing
IP Address spoofing is the act of changing the IP header in a packet to change the source/sender address of the packet. The goal is to mask the identity of the source or put the source as a victim for an attack. A DDoS attack could then be reflected by to the victim in whats known as a Reflected DDoS attack. This is where the attacker generates a lot of fake requests on behalf of the a victim, then victim then receives all the responses.
Preventing Spoofing
Ingress Filtering
Ingress filtering watches all incoming traffic for signs of spoofing and blocks that traffic from reaching the network. E.G.: it will monitor the external inbound traffic for source addresses that match those assigned to internal devices and networks. An internal source address should never appear on the traffic coming from outside of the internal network, so the their presence is a sign of spoofing.
Egress Filtering
Egress filtering watches outbound traffic for a source address that does not belong to your organisation. IF someone is sending a packet from within the network with the source address of a different network, there is the potential that system has been compromised and is being used for malicious purposes.
1.3.5 Cryptographic Attacks
Hash function
A hash function is a mathematical function that takes variable length input and translates it into a fixed length output, in a matter that is collision resistant. The output is called the hash code, hash values, digests or just hashes.
Hash function criteria:
- must produce a completely different output for each input
- must be computationally difficult to retrieve the input from the output (its irreversible)
- must be computationally difficult to find 2 inputs that generate the same output (this is known as a collision)
Hash functions are used in authentication, message integrity, message fingerprinting, data corruption detection, and digital signature efficiency.
The Birthday Problem
Collisions can become a problem with large sample size. This is known as the birthday problem.
What are the odds that 2 people in a room will share the same birth date?
- 100% with 367 people
- 50% with only 23 people
- 99.9% with 70 people
This is known as a collision.
A good link here if you want to go a bit deeper with this:
https://en.wikipedia.org/wiki/Birthday_problem
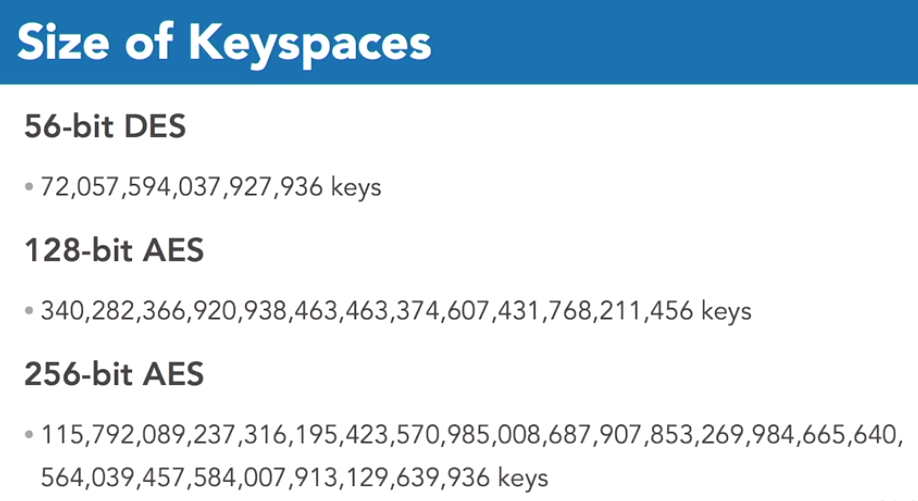
Key space
The key space is the list of possible keys. In a fairly short key, using 56 bits of encryption (such as the outdated data encryption standard, DES) there are 56 digits that may be each a 1 or a 0. this leaves a whopping 72 quadrillion possibilities!
Brute Force Attack
Using a program or script, the attacker “guesses” the password by going through many different combinations of characters. All the attacker needs to begin is a list of usernames (which could easily be retrieved from websites, email lists etc…). This is why users should long complex passwords.
Online Brute Force Attack
This is where the attacker tries to hack into a live system. In this case the attacker might be limited by restrictions on the server, e.g.: a limit on how many times you can try a password.
Offline Brute Force Attack
There is where the attacker has a copy of a password file and take their time trying to hack it.
Dictionary Attacks
In this the attacker uses a program or script and cycles through lists of words (from a dictionary).Using a Passphrase (sequence of words) or using characters that are not a simple variant on a word, are the best ways to defeat this method.
Rainbow Table Attack
This is like a pre-computed dictionary attack that allows the attack to be executed faster. It uses less processing time at the time of the attack, but requires more storage. The attacker first computes a list of password hashes and stores these in a database. It then uses this table to reverse cryptographic hash functions (crack the password hashes).
1.3.6 Cryptographic Attacks
Known Plain Text
This is where the attack has a copy of a plain text password and the encrypted version. Using both of these they can try to work out the key.
Chosen-PlainText Attack
This is where the attacker as the ability to encrypt a string using a selected algorithm and key. The attacker can study the algorithms workings in great detail in an attempt to learn the key being used.
Downgrade Attacks
A Downgrade Attack is when an attacker forces 2 systems that are communicating to use an older and lower quality (less secure) protocol for their communication. These more vulnerable protocols are often in place to allow for backwards compatibility with older systems.
An example of a “Downgrade Attack” was the flaw found in OpenSSL that allowed the attacker use a lower version of TLS between the client and server.
1.3.7 Watering Hole Attacks
This type of attack gets its name from the watering holes animals use in dry climates. They need to go there to drink water, but there may be danger lurking.
Attackers will often use this strategy to attack a particular group (organisation, industry or region).
How it works:
- Attackers profile victims and the type of websites they go to
- attacker tests these websites to see if they can find any vulnerabilities
- When the attacker finds a website they can compromise, they use this to install malicious code, or else use code to redirect the victim to attackers website
There have been many high profile attacks of this type:
- In 2017 attackers in China used this technique by infecting many state websites
https://www.hackread.com/chinese-hackers-data-center-watering-hole-attack/ - Also in 2017, Ccleaner’s website got compromised and attackers infected the Ccleaner application file with a Trojan Horse. When victims downloaded and installed Ccleaner they also installed malware. Security experts think this attack was aimed at some large technology corporations like Samsung, Sony, VMware, Cisco, Linksys, Akamai and DLink.
https://www.eweek.com/security/ccleaner-attack-targeted-telecoms-network-hardware-providers
1.3.8 Wireless Attacks
The Institute of Electrical and Electronics Engineers is responsible for telling the world how to make wifi work, and they do so in a standard document called 802.11.
WiFi uses radio signals that anyone can pluck out of the air with some basic equipment. This makes encryption critical for protecting the security of wireless networks. Encryption hides the content of the traffic on the network from those who don’t have the encryption key.
WiFi Encryption Options
- You opt for no encryption. Obviously this is not a good idea
- Wired Equivalent Privacy (WEP) this uses RC4, a software stream cipher that is vulnerable to attack. This is best avoided
- WiFi Protected Access (WPA) also uses RC4 but it adds the Temporal Key Integrity Protocol (TKIP). TKIP uses the original WEP method but wraps each packet to encapsulate it and modify it. Each packet is encrypted with its own each unique encryption key. This makes discovering the key from monitoring the network difficult
- WiFi Protected Access v2 (WPA2) uses Advanced Encryption Standard (AES) via CCMP (Counter Mode Cipher Block Chaining Message Authentication Code Protocol). This makes it more secure than WEP and WPA and it is currently the best practice. Since 2006 no hardware or device can use the WiFi trademark without recognising the WPA2 certification program
- WPA3 is the latest and safest encryption option. But at the time of writing it is not widely used due to it not being available on many types of hardware. Apparently this version fixes any known vulnerabilities and also helps secure open networks
Hacking WEP
The flaws in WEP make it susceptible to statistical cracking techniques. WEP uses weak keys and it also re-uses keys which is a big weakness in a system. The Initialisation Vector (which is used to initialise the key stream) is only 24 bits and is send in plaintext.
WPA Attacks
WPA is generally safe. Researchers have described some attacks against WPA, however, that use characteristics of TKIP to perform limited decryption of network traffic, and potentially insert unauthorized packets into a network stream.
WPA2 does not use TKIP, so it is not vulnerable to this problem. However it does have its own issues. One such attack is the KRACK attack(Key Reinstallation Attack), which was discovered by security researcher Mathy Vanhoef. This uses information transferred during the handshake between client and access point to hack the system.
WPA3
WPS (WiFi Protected Setup) Attacks
WPS allows quick setup of devices. There are two methods for establishing connection:
1. Pressing buttons on each device and let them establish a connection automatically
2. You can use an 8 digit pin printed on the bottom of the access point
The pin might sound secure. With 8 digits there are 11 million possible PINs which would take a while to guess. But cryptographers discovered a mathematical flaw in the WPS algorithm that makes it easy to guess. Attackers can determins a WPS pin with only 11,000 guesses. Once you have the pin you can easily determine the encryption key and gain access to all communications on the network. It is best to disable WPS on any devices.
Propagation Attacks
The open nature of wireless networks makes them perfect targets for attacks that prey upon radio wave propagation. Attackers can simply use strong antennas and pull signals out of the air for analysis.
Jamming and Interference Attacks
These attacks seek to deny users legitimate access to a wireless network (DoS). Attackers don’t try to gain access to the network or eavesdrop on communications, they simply want to stop other people from using the network. The attacker uses a powerful transmitter and broadcasts a very strong signal that overpowers the legitimate network.
War Driving Attacks
In these attacks the attacker foes around a neighbourhood and grabs any information they can about wireless networks in the area. They do this using some soft of wireless client and software. They look for open networks or ones using weak encryption like WEP. War drivers use special software that automatically collects this information, and can even correlate this with GPS to plot it on a map.
There lots of different tools that can be used for these attacks. One of them is iStumbler for Mac. Another one is the Xirrus tool. There is also a website called wigle.net that has all the different WiFi recorded around the place plotted on a map.
Rogue Access Points
This is when someone connects an unauthorised wireless access point to an enterprise network. This could innocently be an employee bringing in their own P to boost their WiFi signal, or it could be hacker trying to gain access to your network. Rogue Access Points can bypass other authentication you have on your network. they can also cause interference as there are a limited number of WiFi channels available.
Rogue AP Detection
Use software like the Xirrus WiFi Analyser to find rogue APs and locate them.
Evil Twin attacks
This is where the attacker sets up a fake access point with the same SSID of a legitimate network. They then lure unsuspecting users to connect to the attackers network, thinking they are connecting to the legitimate network. Since the attacker controls this network, they can then use tactics like DNS poisoning to redirect users to phishing websites. Conducting an evil twin attack is relatively easy with open networks and very common SSID
Disassociation Attacks
In these attacks the attacker sends a deauthentication frame to the wireless client, dissociating it from the wireless network. The client then has to reconnect and re-authenticate with the network.
Depending on the type of attack, hackers sometimes monitor the authentication process over time to try and gain information that can be used to hack the wireless network. Normally, once a client connects to a network it continues to use that wireless network for an extended period of time without re-authenticating. This means it can be a long period of time before the hacker gathers enough information. They may then use a Disassociation Attack so that the victim has to keep reconnecting and re-authenticating with the network.
Disassociation attacks may also be used as a type of DoS attack.
How a Disassociation Attack Works
During the disassociation process, the Access Point sends a deauthentication frame to the client. This frame has the source MAC of the AP and the destination MAC of the client. Attackers can fake this by spoofing the MAC address of the AP and sending the deauthentication frames from their device. The client receives this frame and believes it came from the legitimate AP and disconnects from the network. An attacker can repeat this many times.
Bluetooth and NFC (Near Field Communication) Attacks
Bluetooth and near field communication share several features, both being forms of wireless communication between devices over short distances. NFC is limited to a distance of approximately four centimetres while Bluetooth can reach over thirty feet. This technology is used for things like: headsets, mobile payments, external speakers, door access and all sorts of other devices. NFC and Bluetooth provides attackers with another pathway to exploit security vulnerabilities.
Bluejacking
This is where the attacker sends Bluetooth spam to the victims device. Te attacker tries to enhance the victim to take some action, usually they try and get them to go to a phishing website or some other action that will lead to a more advanced attack. Bluejacking is rarely used these days but it is on the Security+ exam.
Bluesnarfing
This attack exploited firmware flaws in Bluetooth devices. The attacker forced pairing between the devices, this connection then gives them access to the victims device and its contents. The could also monitor the communications taking place on the victims device.
Defending against Bluetooth and NFC attacks
- turn off Bluetooth when not in use
- Ensure OS and firmware is patched and up to date
- Be aware of any suspicious activity on your phone
RFID Security
Radio Frequency Identification (RFID) chips are widely used in organisations today for a number of different uses. There are RFID chips embedded in lots of devices. When this RFID chip comes in proximity of an RFID scanner, the chip activates and sends information to the scanner.
Examples of use:
- New passports have RFID chips that allow border agents to access digital information about the passport holder
- transit cards (Myki) and credit/debit cards often use RFID to allow for contactless reading
- Electronic toll systems
- Door access systems
- Warehouses track stock with RFID tags
- Shops and libraries use RFID tags for security measures
RFID Security Concerns
- Business want strong authentication and encryption to protect the integrity of RFID systems. EG: someone could generate a fake toll pass which they could then use to travel through tolls and charge to someone else
- Consumers want privacy safeguards to protect their personal information, EG: passport information.



3 thoughts on “Security+ Course – 1.3 Understanding Attack Types”