Contents
2.3.1 Firewall Rule Management
Basic function of a firewall:
- someone from outside the network attempts to connect to a device inside the protected network
- firewall consults a ilst of rules maintained by the administrator
- if it finds a rule that matches the description of the attempted connection, it follows the action specified by that rule (it can allow it or deny it depending on the rule)
- if it doesn’t have a rule matching this attempted connection, it follows the default deny principle and blocks that traffic
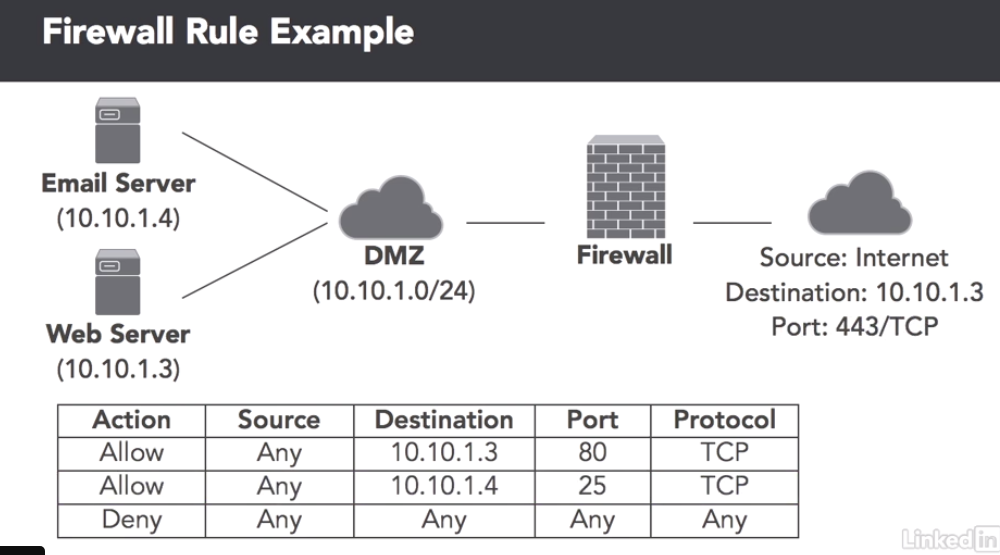
Firewall rules work from top to bottom, i.e.: checks the traffic against rule 1, then rule 2 etc… until it is eventually allowed through or it gets blocked.
Shadowed Rules
This is when a more broad rule is above a more specific rule. This means all traffic will caught by the more broad rule before it reaches the more specific rule. The specific rules should be above the broad rules.
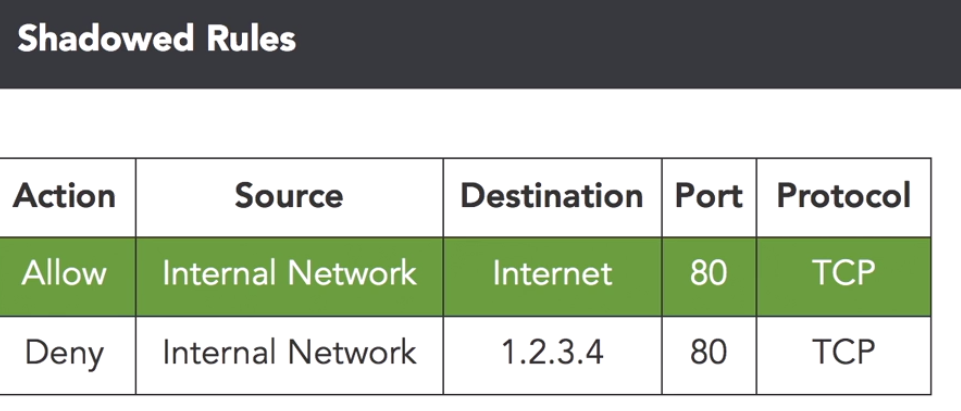
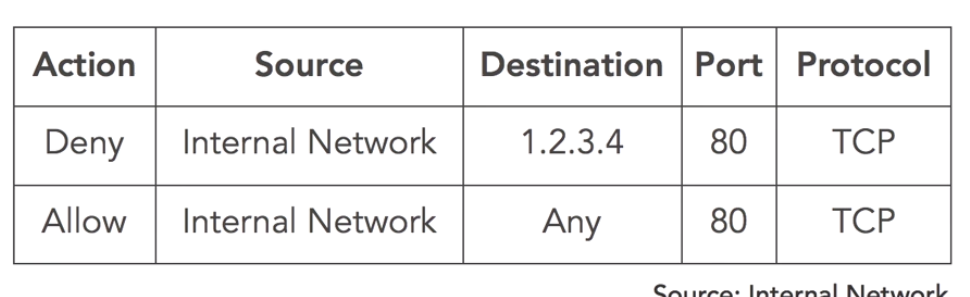
In the example above they are trying to block access from the internal network to a malicious server (IP:1.2.3.4). But if the rules are in this order it will never get blocked because the rule above says allow all traffic to the internet. This can easily fixed by re-arranging the order of the rules:
Promiscuous Rules
These are rules that allow more than necessary. There are a number of reasons promiscuous rules could be in place:
- Laziness
- Lack of understanding of how the system works
- A simple typo
Orphaned Rules
These occur when a system or service is decommissioned but the rules for these systems are never removed on the firewall.
EG: the organisation has a server behind a firewall that is accessible on port 80 from the web. The server is then decommissioned but the rule is left in place. The danger is that the IP that the server had could be reused for something else, then whatever has that IP is open to the web.
2.3.2 Router Configuration Security
Routers often sit in front of network firewalls and can perform basic filtering that can reduce the load on the firewall.
Router Access Control Lists
Standard Access Control List: this performs filtering based upon the source IP address.
Extended Access Control Lists: these perform filtering based upon more advanced criteria, such as:
- Source and destination IP’s
- Source and destination ports
- Protocol used in the communication
Firewalls Vs Routers
There are a number of differences between firewalls and routers:
- Firewalls are purpose specific and are much more efficient at performing complex filtering than routers
- Firewalls have advanced rule capabilities. You can create rules depending on the time of day, the users involved etc…
- Firewalls offer more advanced security functionality. They can incorporate threat intelligence, application inspection and integrate with Intrusion Prevention Systems
2.3.3 Switch Configuration Security
Physical Switch Security
If an attacker has physical access to your switch they can control that portion of the network (i.e.: take it offline or mess with it).
VLAN Security
VLAN common practices:
- Disable automatic trunk negotiation to prevent VLAN hopping attacks. An attacker could maliciously use this by pretending to be a switch, then the legitimate witch trunks its VLANs to the malicious device
- VLAN Pruning: only trunk the VLANs to the switch that are required. This reduces the risk of someone getting access to a VLAN that they shouldn’t
- Port Security: this is like an ACL for MAC addresses that can be used on a particular switch port. If a device is switched out the administrator needs to change the ACL to allow the new MAC address connect to the network. This prevents an attacker from plugging in a malicious device to the network such as an eavesdropping. There are 2 port security modes:
Static: the administrator manually configures each port with the allowed MAC addresses for that port
Sticky or Dynamic: the switch memorises the first MAC address it sees and then restricts access to that MAC address
2.3.4 Maintaining Network Availability
Sometimes attackers try to undermine network security by denying legitimate users access to the network.
Flooding Attacks
In this the attacker sends thousands of SYN requests to the target system in an attempt to consume enough server resources to make the system unresponsive to legitimate traffic.
Defending Against These Attacks: Flood Guard Protection works by controlling the number of open connection each source system can have
MAC Flooding Attack
In this method the attacker sends a large number of MAC addresses to the switch in the hope of filling the switches MAC address table with illegitimate information. Once the switch is full of illegitimate information it will no longer have the MAC addresses of the actual attached devices. This will cause the switch broadcast packets out to all the ports. The attacker can then eavesdrop on these packets trying to find some sensitive information.
Defending Against These Attacks: Port Security helps prevent MAC flooding as the switch only learns the MAC addresses of certain devices.
Routing Loops
These occur when there are 2 or more physical paths between two network devices and the devices begin broadcasting traffic in a loop to each other.They can quickly consume all the network resources and allow no capacity for legitimate end users.
Preventing Routing Loops: the Spanning Tree Protocol helps prevent these loops. STP blocks the port of there is a loop, but then unblocks the port if it is needed (in case the other port to the network device fails).
2.3.5 Monitoring Network Logs
Log files can be very useful for investigating network issues.
Firewall Logs
These log details include:
- Details about attempted connections
- Source and destination ports and IP addresses
- A timestamp
- Identity of the firewall rule that either blocked or allowed the connection
Netflow
This is like a skimmed down packet capture. It is sort of like an itemised phone bill, it doesn’t show the actual communication, just the summary of the details. It tells you:
- Which systems communicated
- When they communicated
- How much data they exchanged
Security Information and Event Management Systems (SIEM)
Going through log files can be a tedious task. Usually this involves logging on to different servers or switches and going through the logs. But SIEM systems can automate a lot of this. They compile log files from a lot of different sources, including:
- Firewalls
- Network devices
- Servers
- Applications
You can then filter through the compiled log files to find what you are looking for.
2.3.6 SNMP – Simple Network Management Protocol
This provides administrators a means to centrally monitor and configure devices.
SNMP Components
The SNMP Agent is a piece of software that runs on the managed device (server, switch, firewall, router, etc…) and allows it to communicate with the SNMP service. Most often the agent is built into the network devices software.
The Network Management System is the central system that communicates with the SNMP agents. This is the server that they send their information to. It reaches out to the agents (sends a Get Request) on a periodic basis and requests the information it is configured to receive. The agent then sends this information back (SNMP Response).
The Network Management System can also (if configured to) send some configuration settings to the agents. This is called a Set Request. The agent will then send an SNMP response back saying if the configuration was successful or not.
The agents may also be able to initiate communication with the Network Management System. This could be in the case of an error like a port going down. In this case the agents sends an SNMP Trap to the network management system. The Network Management System can then alert the administrator.
SNMPv3
This is the latest version and should always be used as previous versions have known vulnerabilities (including sending passwords in plain-text).
2.3.7 Storage Networks
Storage networks are used for bandwidth intensive communications between computing systems and the storage arrays attached to them.
Network Attached Storage (NAS)
These are storage devices connected to a network that provide storage to other devices on the network. They are simple self contained storage devices that commonly use CIFS and NFS.
Storage Area Networks (SAN)
Larger storage needs require the use of SAN’s. These are massive arrays of storage devices that serve networks with very large storage requirements. SANs present raw storage to devices rather than file systems. The Operating system can use it as it wishes. SANs are connected using dedicated storage networks.
SAN Connection Types:
- Fibre channel: uses direct fibre connections between the SAN and devices
- FC (Fibre channel) over Ethernet: replaces fibre optic cables with Ethernet links
- iSCSI: runs the SCSI standard over network connections
Storage Network Security
Storage networks carry sensitive information often in unencrypted form. Storage should be carried on a dedicated network or use a separate VLAN that has careful trunk management to ensure it is only available where it i absolutely needed.
