Contents
1. Data Encryption Standard (DES)
DES was designed by IBM in the 1970’s Intended to serve as a federal encryption standard. Up until that point different agencies used different encryption algorithms. This caused issues with security because all of those algorithms weren’t thoroughly tested, and interoperability because different agencies couldn’t easily communicate with each other
How DES Works
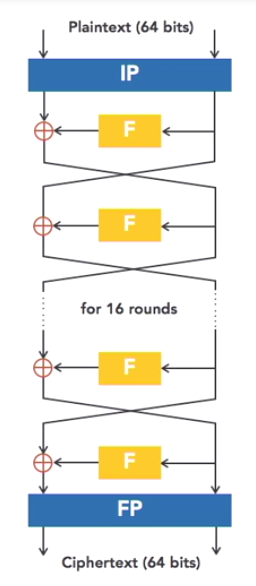
DES uses an encryption operation called the Feistel function for 16 rounds of encryption.
In this diagram below you can see the plaintext enters the top and is run through Feistel (F boxes) 16 times, then at the bottom emerges the ciphertext.
Each of these F boxes that implements the Feistel function, takes half a block of input, or 32 bits, and combines it with a piece of the 56-bit encryption key. Then the output of that function is broken up into eight segments and fed into eight different functions called S boxes, these yellow boxes labelled S1 through S8 in the next diagram. S stands for Substitution and each one of these boxes contains a different substitution cipher. The results of all of those substitutions are then combined back together again and fed into a P box. P stands for Permutation which is just another term for transposition. The output of all of those S boxes is scrambled up to produce the cipher text.
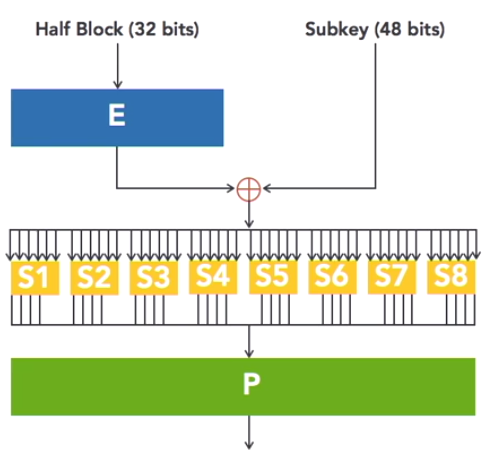
Remember, this happens inside each F box, so that has happens 16 times on any block of input.
No Longer Secure
DES was used widely throughout the government and the private sector for decades. But today, it is no longer considered secure. Mathematicians and cryptologists have published papers containing several effective attacks against the DES algorithm and it is no longer recommended for use.
Key facts about DES
- symmetric encryption algorithm
- It is a block cipher working on 64-bit blocks
- use a 56-bit key
- is now considered insecure
2. Triple DES (3DES)
When researchers discovered a DES was insecure, security professionals faced a dilemma. They had tons of old equipment designed to work with DES, but were no longer able to rely upon its security. While the government worked to adopt to the new advanced encryption standard, AES, practical security professionals around the world discovered a workaround. By using the DES algorithm on the same text multiple times, they could achieve greater security.
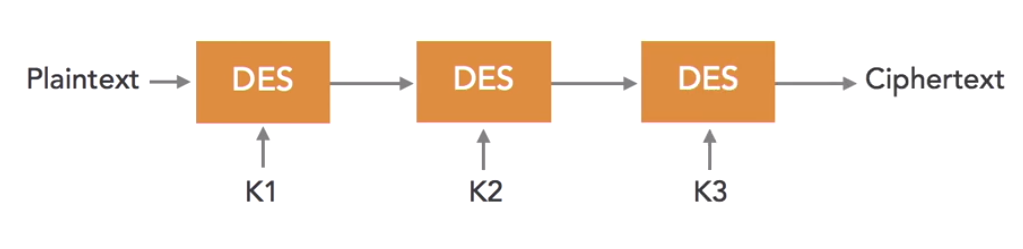
How 3DES Works
This method applies DES three times with three keys: K1, K2 and K3
3DES Key Options
Option 1: All 3 keys are different. This is the strongest approach and results an encryption with an effective key strength of 112 bits.
Option 2: keys one and three are the same. This requires fewer keys, but reduces the strength of the algorithm from 112 bits down to 80 bits
Option 3: All three keys are the same. This emulates the standard DES algorithm and is just as insecure as that standard approach. It is included for backwards compatibility with DES, but is definitely not a good option
3DES Security
Triple DES is still widely used today and is considered a secure algorithm when used in keying mode one. The National Institute for Standards and Technology considers keying mode one secure for use through at least the year 2030.
Key Facts about 3DES
- symmetric encryption algorithm
- block cipher that works on 64-bit blocks
- effective key length of 112 bits
- still considered secure today.
3. AES
The Advanced Encryption Standard, or AES, came as the result of a competition led by the National Institute for Standards and Technology. The winner was an algorithm called Rijndael which is now better known as AES. Like DES, AES uses a combination of substitution and transposition functions to achieve strong encryption. It is widely used today in many different cryptographic applications ranging from web security to encrypted voice communications.
You can run aescrypt on most platforms to encrypt files. https://www.aescrypt.com/
High-level description of the AES algorithm
From: https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
- KeyExpansion – round keys are derived from the cipher key using the AES key schedule (expand a short key into a number of separate round key). AES requires a separate 128-bit round key block for each round plus one more.
- Initial round key addition:
AddRoundKey – each byte of the state is combined with a byte of the round key using bitwise xor. - 9, 11 or 13 rounds:
a) SubBytes – a non-linear substitution step where each byte is replaced with another according to a lookup table.
b) ShiftRows – a transposition step where the last three rows of the state are shifted cyclically a certain number of steps.
c) MixColumns – a linear mixing operation which operates on the columns of the state, combining the four bytes in each column.
d) AddRoundKey - Final round (making 10, 12 or 14 rounds in total):
a) SubBytes
b) ShiftRows
c) AddRoundKey
Key Facts about AES
- Symmetric encryption algorithm
- block cipher that works on 128-bit blocks
- allows for three different key lengths: 128-bit key, a 192-bit key, or a 256-bit key
- All three of these options are considered secure today
4. Blowfish
Like DES and AES, Blowfish uses a Feistel network that combines both substitution and transposition operations. It is a completely public domain algorithm developed by cryptography expert Bruce Schneier in 1993 as a potential replacement for the Data Encryption Standard.
Key Facts about Blowfish
- Symmetric encryption algorithm
- block cipher that works on 64-bit blocks
- Allows any key length between 32 and 448 bits
- Not considered secure anymore (Schneier now recommends twofish instead)
5. Twofish
Twofish relies on a Feistel network for secrecy that combines substitution and transposition. It was one of the competitors in the AES competition that eventually lost out to the Rijndael algorithm.
Key Facts about Twofish
- Symmetric encryption algorithm
- block cipher that works on 128-bit blocks
- allows for three different key lengths: 128-bit key, a 192-bit key, or a 256-bit key
- Still considered secure today
6. RC4
RC4 is a symmetric stream cipher that was widely used to encrypt network communications.
RC4 was used in the following:
- Wired Equivalent Privacy (WEP)
- Wi-Fi Protected Access (WPA)
- Secure Sockets Layer (SSL)
- Transport Layer Security (TLS)
The RC4 stream cipher works by creating a stream of bits to use as the encryption key. This stream has many of the qualities of a random string, but it is not quite random because it is initialised using a selected encryption key. This makes it possible for both the sender and recipient of a message to use the same key to generate the same keystream.
The algorithm reached an unfortunate tipping point in 2015 when security researchers demonstrated a series of fatal flaws in RC4. It is now widely believed that government intelligence agencies may have the ability to break RC4 encryption and most security professionals recommend against using the algorithm.
Key Facts about RC4
- Symmetric encryption algorithm
- Stream cipher
- Variable key length between 40 and 2048 bits
- No longer considered secure
7. Cipher Modes
A Cipher Mode describes how an algorithm encrypts and decrypts data.
Electronic Codebook Mode (ECB)
This is perhaps the most straightforward cipher mode. The algorithm simulates a digital codebook that provides an encrypted version of each possible input.
For example, if we have a message of 192 bits that we want to encrypt, and are using a 64-bit block cipher, the algorithm breaks the message up into three blocks and handles each of them completely independently. It takes the first block and uses the encryption algorithm to encrypt that block with the encryption key. That creates the first ciphertext block. It then moves on to the second block and encrypts it with the same key, and then repeats the same process for the third block.
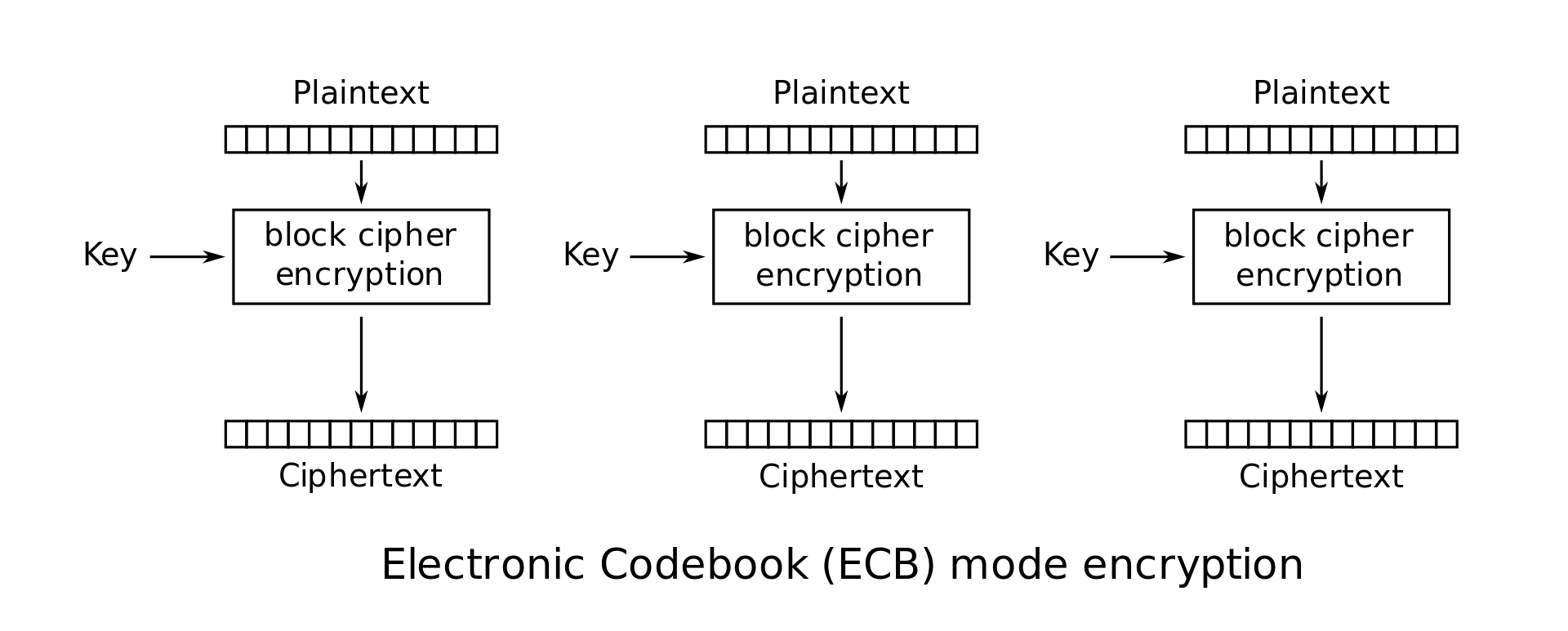
https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation
If you encrypt the same block with the same key multiple times using ECB mode, you will get the same ciphertext each time. This is the key disadvantage of this mode, as it makes cryptoanalysis easier.
Cipher Block Chaining Mode (CBC)
CBC seeks to resolve this disadvantage of EBC by making the encryption of a block dependent upon the encryption of all previous blocks. CBC does this by feeding the previous encrypted block into the encryption of the next block.
We begin in the same way as ECB mode. Breaking our plaintext into blocks. We then combine the first block with an initialisation vector using the exclusive OR operation. This initialisation vector is just to get us started. The algorithm then uses the encryption key to encrypt the XORed combination of the plaintext and the initialisation vector to get the ciphertext block. Then, when we move on to the second block, instead of using the initialisation vector, we XOR the second plaintext block with the first ciphertext block and then encrypt that combination to get the second ciphertext block.
We then move on to the third plaintext block, where the second encrypted block is then combined with the third plaintext block, and encrypted to get the third ciphertext block. And the process continues on, until we run out plaintext blocks.

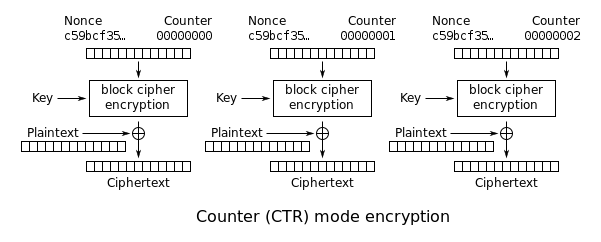
Counter Mode (CTR)
CTR mode performs the encryption a little differently. It begins with a plaintext, and two values. A randomly generated value, known as a nonce. And a counter, that begins at zero, and increments during each encryption operation. The value created by the nonce and the counter is then encrypted with the encryption key, and the resulting value is XORed with the plaintext to get the cipher text. When we get to the second block, the counter value is incremented to one, and we repeat the previous operation to get the second ciphertext block. And we then do the same thing for the third block, with a counter value of two to get the final ciphertext block.