Contents
1. Rivest-Shamir-Adleman (RSA)
Asymmetric cryptography solves issues of scalability by giving each user a pair of keys for use in encryption and decryption operations. The RSA algorithm was one of the earliest asymmetric cryptographic algorithms and it is still used today. It was published in 1977.
There’s a lot of complex maths involved in creating that key pair, but the underlying principle that you need to understand is that a user selects two very large prime numbers that are used to create the encryption keys. After going through some mathematical computation, RSA uses the prime numbers to create a public and a private key.
EXAM TIP: users create RSA key pairs using two large prime numbers
As with any asymmetric algorithm, the user is then responsible for keeping the private key secure and distributing the public key to other people with whom he or she wishes to communicate.
RSA Keys
- Sender encrypts message using the recipients public key
- Recipient decrypts message using the recipients private key
The major drawback to the RSA algorithm is that it is fairly slow. Therefore, it is not normally used for exchanging long messages directly between communicating systems. Instead, RSA is often used to create an initial secure communications channel over which two systems exchange a symmetric key.
Key facts about RSA
- Asymmetric encryption algorithm
- Variable length key between 1024 and 4096 bits
- Considered secure (when used with sufficiently long key)
2. PGP and GnuPG
Pretty Good Privacy (PGP)
Phil Zimmerman created PGP in 1991. PGP is still widely used today and the details are still freely available for anyone to use through the OpenPGP standard.
PGP Use
Uses public and private key pairs
It combines both symmetric and asymmetric cryptography
PGP Encryption
The sender of a message has the original plain text and then generates a random symmetric encryption key. Next, the sender encrypts the message using that random symmetric key, and then encrypts the random key using the recipient’s public key. The sender then transmits the encrypted message which is a combination of the encrypted data and the encrypted random key.
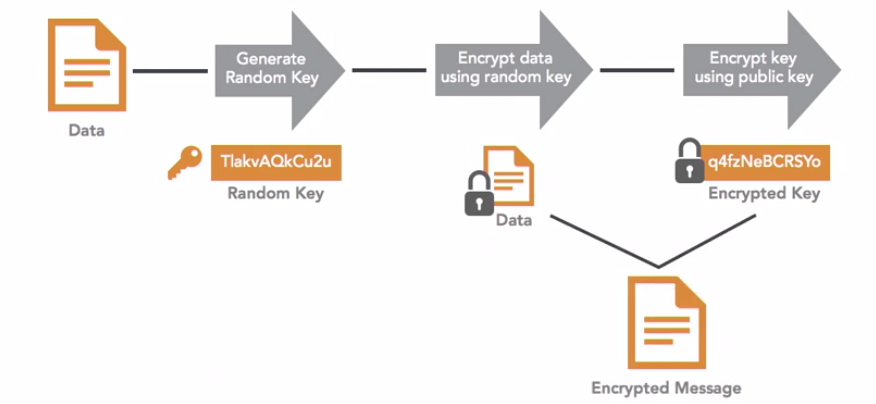
PGP Decryption
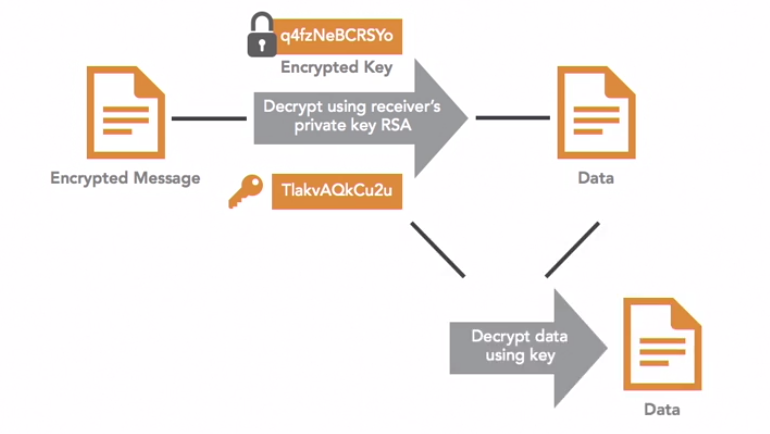
First, the recipient decrypts the encrypted random key using the recipient’s private key. This produces the random key created by the sender. Next, the recipient uses that random key to decrypt the encrypted message the encrypted message and retrieve the original message. and retrieve the original message.
- PGP is a commercial product
- GnuPG is an open source application
Using GPG
- The trainer ran through an example of using GPG. Here are the high level steps
- Alice (sender) generates a pair of encryption keys. During this process it asks for her ID (email) and a passphrase. It also asks the type of encryption algorithm you would like to use
- Bob (recipient) generates a pair of encryption keys. During this process it asks for his ID (email) and a passphrase
- Now Bob needs to get his public key to Alice. This can be done via encrypted email, usb drive etc…
- Alice then imports this key using GPG
- Alice then uses the GPG command to encrypt the file
- It asks for a recipient ID and she enters Bob’s email (it seems this is how it knows to use his imported key)
- It then encrypts the message
- Alice then sends this to Bob. She can send it how she likes as only he has the key to decrypt it.
- Bob then decrypts the message using the command: gpg –decrypt filename
- It asks him for his passphrase associates with the private key
- It then decrypts the message
NB: PGP is not an encryption algorithm itself, it is a framework for using other encryption algorithms
3. Elliptic Curve and Quantum Cryptography
These are covered on the exam but are less commonly used.
Factoring Prime Numbers
All public key, or asymmetric cryptography is based upon the difficulty of solving complex mathematical problems. In the case of the RSA algorithm, the security of the algorithm depends upon the difficulty of factoring the product of two large prime numbers.
Factoring some prime numbers can be easy, as in these examples:

But factoring larger numbers can be much more difficult:
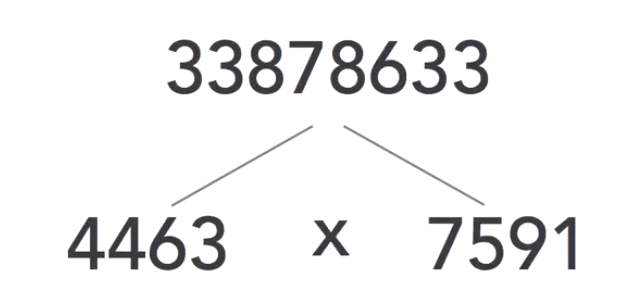
Currently, there is no known effective way to solve the prime factorisation problem efficiently for large prime numbers. If someone discovered an efficient way to do this, all the cryptographic algorithms that depend upon prime factorisation would immediately become insecure.
Elliptic Curve Cryptography (ECC)
This does not depend upon the prime factorisation problem it uses a completely different problem known as the elliptic curve discrete logarithm problem. Understanding that problem is a little more difficult than the prime factorisation problem but fortunately, we don’t need to understand how ECC works on the exam. Just remember that ECC uses a different approach than the prime factorisation problem.
Quantum Computing
Quantum computing is an emerging field that attempts to use quantum mechanics to perform computing tasks. It is still mostly a theoretical field. But if it advances to the point where that theory becomes practical to implement, quantum cryptography may be able to defeat cryptographic algorithms that depend upon factoring large prime numbers. Unfortunately, the use of elliptic curve cryptography would not provide protection against quantum attacks. At the same time, quantum computing may be used to develop even stronger cryptographic algorithms that would be far more secure than modern approaches.
4. Tor and Perfect Forward Secrecy
TOR
Tor is a software package that provides an anonymous, secure way for individuals to access the internet. Tor also enables access to anonymous websites that are commonly known as the dark web. Tor, which stands for the Onion Router, uses encryption and relay nodes to hide the true sources and destinations of network communications. Tor is widely used in the security community, and was made popular by NSA leaker Edward Snowden when he used it to transfer secrets to the Washington post and other media outlets in 2013.
How Tor Works
In this example, Alice, who wishes to visit the Washington Post, but doesn’t want that website to know her identity. She also doesn’t want anyone along the way to know who she is.
- Alice opens a Tor browser on her computer, and types in the websites URL, washingtonpost.com.
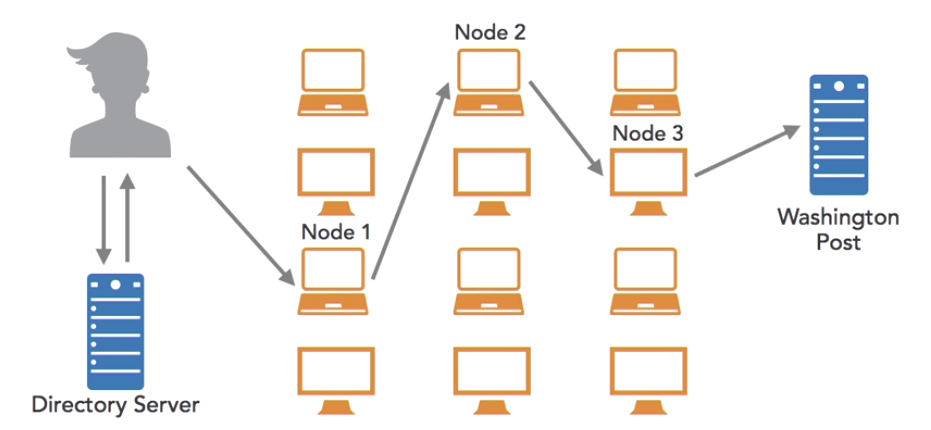
- Alice’s Tor browser then accesses a Tor directory server and loads a list of all of the Tor nodes currently available on the internet. This is a long list of over 7000 relay nodes. Each of these nodes is an individual computer system whose owner has placed it at the service of the Tor network. The owner doesn’t receive any compensation for this. He or she simply wants to contribute to providing anonymized web surfing.
- Alice’s broswer randomly selects a series of nodes, usually three, that are used to route traffic to its final destination. Each node involved in the process only knows the identity of the node before and after it.
- When Alice sends her request to node one, node one knows that the request came from Alice, and it also knows that the next step in the process is to sent it to node two, but it doesn’t know that the Washington Post is the final destination.
- When node two receives the request, it knows that it came from node one, and that it’s headed next to node three. But node two doesn’t know Alice’s identity, or the fact that the communication involves the Washington Post
- When node three receives the message, it knows that the request came from node two, and it knows that it needs to send the request on to the Washington Post. But node three does not know that either Alice, or node one was involved
- When the request does arrive at the Washington Post server, it looks just like any other request that the website receives, but it appears to have come from node three, and it doesn’t provide Alice’s identity.
This preserves the anonymity of the communication, and enforces something known as perfect forward secrecy, or PFS
Perfect Forward Secrecy (PFR)
Perfect forward secrecy uses encryption to hide the details of the communication from the participants in the communication, ensuring that each node only knows the identity of the node immediately before, and after it in the process.
How PFR Works
- Alice creates the original request addressed to the Washington Post, and seals it inside a virtual envelope by encrypting it, so that it may only be read by node three
- Alice’s browser then takes that envelope, and puts it inside another envelope addressed to node three, encrypting that envelope so that it may only be read by node two
- Finally, that last envelope is sealed inside one more envelope that’s addressed to node one
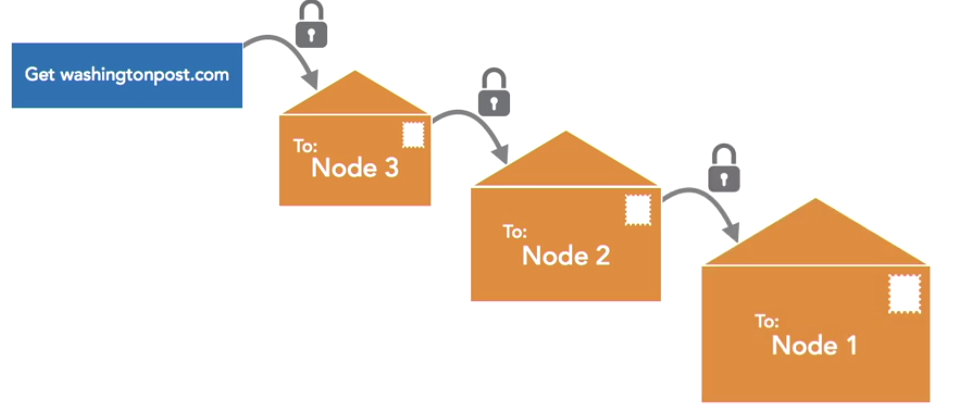
- When node one receives the request, it opens the first envelope because it has the needed decryption key. It can’t open the next envelope because it doesn’t have node two’s key, so it takes that second envelope and passes it on to node two
- Node two does have the correct key. Node two then opens that envelope and finds inside an envelope addressed to node three, and passes that along to node three
- Node three opens that final envelope, and then sends the true request along to the Washington Post’s server
Hidden Sites
Tor also provides the ability to have two-way anonymity, so that the user doesn’t know the location of the website either. That’s a function known as ‘hidden sites’ in Tor. They have very strange URLs They use long, unique identifiers, and then end in .onion. An example is a service known as SecureDrop. This site is actually run by the Washington Post. It’s a hidden site on the dark net that allows sources who wish to send confidential information to the Washington Post to do so with complete anonymity. The SecureDrop service is an open-source package used by many different journalists, and from different outlets. It allows whistleblowers to communicate completely anonymously with them over the Tor network. Tor has its fans, but it also has its enemies.
Privacy advocates praise Tor because it does allow completely anonymous activity online. Law enforcement officials do not like Tor very much, because that anonymity may be used to hide criminal activity.
