Contents
1. Key Exchange
In symmetric encryption, the sender and receiver share a single secret key that nobody else should know. Before the sender and receiver can begin to communicate using a symmetric algorithm, they must somehow agree upon and exchange the shared secret key that they will use for that communication session.
Problems with Key exchange
EG: Alice and Bob are trying to communicate secretly. Alice is going to create the key and send it to Bob
- When sending the key to Bob someone could intercept it and eavesdrop on the communication
- Someone could impersonate Alice and send a fake key to Bob
Methods of exchanging a key
- Physically handing it over on a USB
- Giving it over the phone
- Use an in band key exchange algorithm (next section)
2. Diffie-Hellman Key Exchange
This key exchange algorithm solves the problem of key exchange for symmetric algorithms. The algorithm was invented in 1976 by three cryptographers. It was based upon the work of Ralph Merkle and turned into a practical algorithm by Whitfield Diffie and Martin Hellman. Unfortunately for Merkle, his name was never included in the popular name used for the algorithm and we’re left with what’s called the Diffie-Hellman algorithm.
How it works
This method uses a complicated maths algorithm.:
- Alice selects 2 common values that she sends to Bob (p and g). One of these must be a prime number
- Alice and Bob both select their own secret number (a and b)
- Alice performs a calculation on her common values and secret number using a defined formula and gets a result (A). She sends the result to Bob.
- Bob performs a calculation on his own secret number and the common values and gets a result (B). He sends this to Alice
- Alice performs another calculation on B and gets her answer 9 (called S)
- Bob performs another calculation on A and gets his answer 9 (called S)
- This is their shared secret key
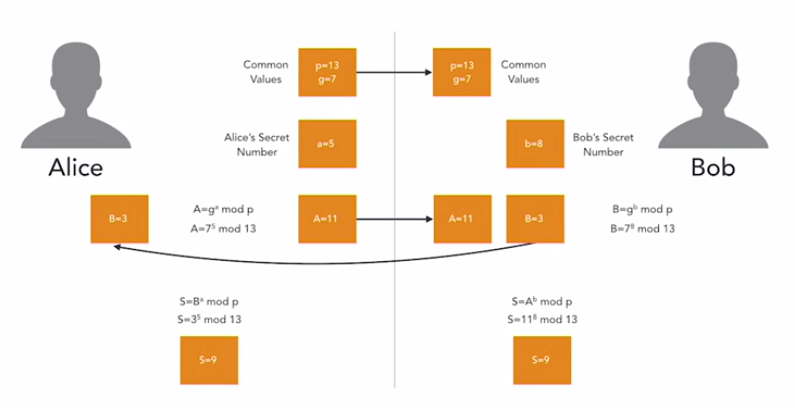
EXAM TIP: in reality the key values must be much higher which makes the maths and the algorithm much more complicated and secure
Elliptic Curve Diffie Hellman (ECDH)
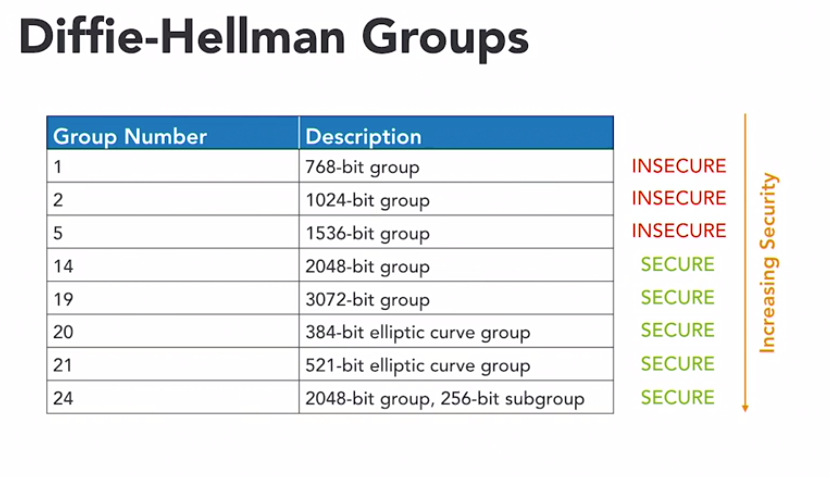
ECDH, algorithm uses a similar approach, but replaces the prime factorisation difficulty with complexity drawn from the elliptic curve problem. Diffie-Hellman algorithms use the concept of groups to describe key strength. Here’s a listing of the common Diffie-Hellman groups. The higher the group number, the more secure the use of Diffie-Hellman. Group 14 is the lowest numbered group that is considered secure. You should not use Diffie-Hellman groups with numbers under 14.
3. Key Escrow and Recovery
Key Escrow
Key escrow is an arrangement in which the keys needed to decrypt encrypted data are held in escrow so that, under certain circumstances, an authorised third party may gain access to those
The idea is that government agents would have to obtain a court order before accessing escrowed keys, thus protecting the privacy of other individuals. While this may be a reasonable goal, there is not yet a reasonable way to implement this approach in a secure manner.
Perhaps the most concerted effort to deploy key escrow technology occurred in 1993, when the government proposed a technology known as the Clipper chip. The chip performed encryption, but also included a special law enforcement access field, or LEAF value, that allowed government agents to access the content of the communication. The Clipper chip caused a tremendous public controversy, as groups like the Electronic Frontier Foundation joined forces with security firms like RSA, to campaign publicly against the Clipper chip’s government back door.
In 2016, the FBI demanded that Apple assist in gaining access to an encrypted iPhone, that the government was using as evidence in a criminal investigation. Apple objected to this request on the grounds that weakening the security of the iPhone encryption software would jeopardise the security of millions of iPhone users.
Recovery Agents
Organisations sometimes have the need to recover the encryption key of a user from within that organisation. This may be simply because the user has forgotten his or her password, or perhaps the user left the organisation and business leaders need to access information encrypted with that key. Some encryption products, such as the Microsoft Windows encrypting file system -EFS- provide for the use of a recovery agent in these scenarios. The recover agent possesses a master encryption key that may decrypt any information used by the organisation. That key must be protected carefully, as it allows global access to all encrypted data in the organisation.
4. Key Stretching
The basic idea behind key stretching is that an algorithm takes a relatively insecure value such as a password and manipulates it in a way that makes it stronger and more resilient to threats like dictionary attacks
Key Stretching Techniques
- Salting: adds a value to the encryption key to make it more complex
- Hashing: adds time to the verification process by requiring more maths. This might be less than a second, but key stretching algorithms repeat this process hundreds or thousands of times to consume longer amounts of time.
Key Stretching Algorithms
- Password-Based Key Derivation Function v2 (PBKDF2): this uses salting and hashing to stretch a key. It is recommended to use its salt-hash process at least 4000 times for security
- Bcrypt: this is based upon the Blowfish cipher and uses that algorithm’s hashing approach combined with a salt to strengthen keys.
