Contents
1. Understanding Encryption
Cryptography is the use of mathematical algorithms to transform information into a form that is not readable by unauthorised individuals. Cryptography does, however, provide authorised individuals with the ability to transform that encrypted information back into readable form.
Encryption: converts information from its plaintext form into an encrypted version that is unreadable. This is known as ciphertext
Decryption: performs the reverse transformation using an algorithm to transform that encrypted ciphertext back into plaintext format.
Algorithms: they are simply a set of mathematical instructions that one follows to achieve a desired result. Like a mathematical recipe
Encryption Algorithms
Encryption algorithms have two inputs.
- Input: P, the plaintext message
- Input: K, the encryption key
- Perform the encryption steps using P and K
- Output: C, the encrypted ciphertext
Decryption Algorithms
Decryption algorithms perform the reverse operation.
- Input: C, the encrypted ciphertext
- Input: K, the decryption key
- Perform decryption steps using C and K
- Output: P, the plaintext message
2. Symmetric and Asymmetric Cryptography
Symmetric Algorithms
This is also known as shared secret encryption algorithms. The encryption and decryption operations use the same key. EG: If one user encrypts a message using the secret key apple, the second user would then decrypt the message using that same key, apple. It’s a shared secret.
This works great when we have two people involved. They can simply agree on an encryption key and then use it to communicate with each other. But if more people are involved, there has to be a shared secret key between each pair.
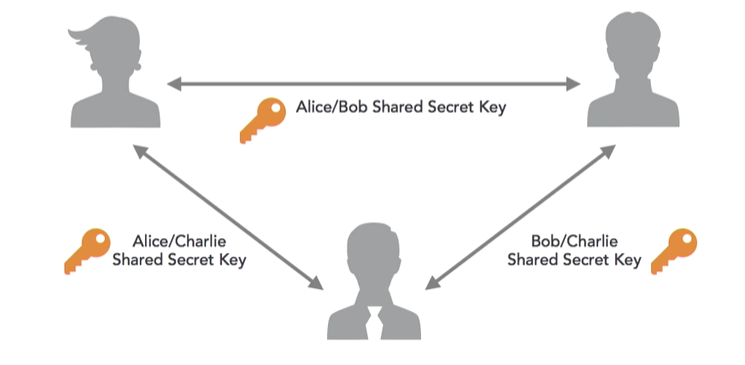
When there are lots of people involved this can turn into a lot of shared secret keys:
The formula for working out the number of keys required is:
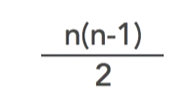
N is the number of people who wish to communicate.
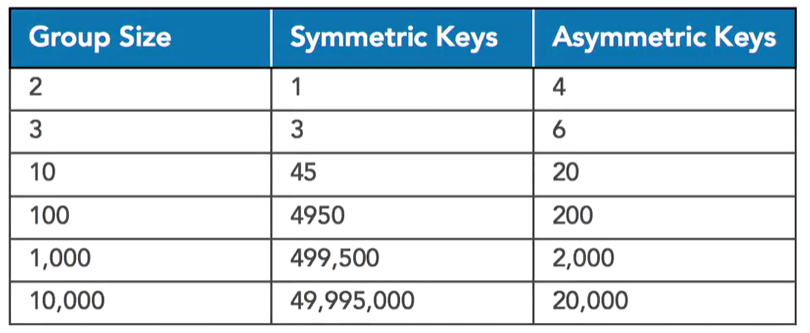
If we have an organisation with 10,000 employees we’d need almost 50 million encryption keys!
If a new person joins the organisation, we’d need to generate 10,000 new keys for that one person to be able to communicate with the other employees in the organisation. And then we’d need to distribute those 10,000 keys to every other employee in the organisation.
Asymmetric Algorithms
- use different keys for encryption and decryption
- also known as public key encryption algorithms
- uses the concept of a key pair
This solves the problem with the number shared secret keys in symmetric cryptography by using he concept of key pairs.
1. Public key: freely distributed to everyone with whom the user would like to communicate
2. Private key: held in secret by the user and not disclosed to anyone else.
In asymmetric cryptography, anything that is encrypted with one key from the pair, can be decrypted with the other key from that pair. For normal communications, the sender of the message would encrypt it with the recipient’s public key, which is publicly known. The recipient would then use his or her private key to decrypt the message.
Asymmetric cryptography is slower than symmetric, but also more scalable. It solves the problem of needing a large amount of keys for a large organisation.
Exam tip: Remember that in asymmetric cryptography, the keys must be from the same pair.
If Bob encrypts a message for Alice, he uses Alice’s public key, and then Alice uses her own private key to decrypt the message, because Alice’s public and private key come from the same pair.
3. Goals of Cryptography
1. Confidentiality: ensures that unauthorised individuals are not able to gain access to sensitive information. Encryption can be used to protect the confidentiality of data in its 3 states:
– at rest (stored on a hard drive)
– in motion (being transferred across a network)
– in use (in memory being used by an application)
2. Integrity: this protects messages and other content against unauthorised modification.
If Alice and Bob are communicating with each other, they want to make sure that Claire is not able to tamper with the message. Bob wants to know that the message he received claiming to be from Alice, is actually the message that Alice sent.
3. Authentication: Proof of identity. Many systems that verify the identity of users rely on the use of encryption.
4. Nonrepudiation: this means that the recipient of a message can prove to an independent third-party that the message actually came from the alleged sender. For example, if Alice sends a message to Bob using an encryption algorithm that supports nonrepudiation, Bob could then show the message to Charlie and prove that the message actually came from Alice and that he didn’t simply create it himself. The technology that we use to achieve nonrepudiation is called digital signature. Nonrepudiation is only possible with asymmetric encryption algorithms.
4. Codes and Ciphers
EXAM TIP: Codes and Ciphers are different things and you need to know the difference!
Code
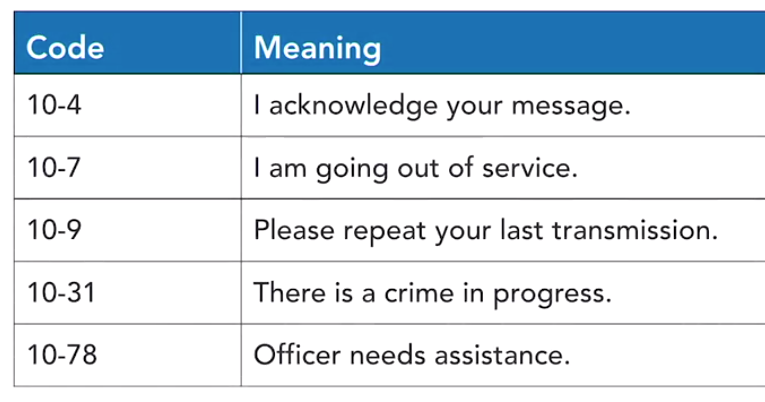
A code is a system that substitutes one meaningful word or phrase for another. This might be done for secrecy purposes or it might be done for efficiency of communication, allowing a short message to convey a detailed meaning. One example of a code that you’ve probably heard about is the ten code system used by police and other organisations who communicate by radio. They have a long list of codes that allow the person sending the message to simply say two numbers and convey a long meaning.
Ciphers
Ciphers use mathematical algorithms to encrypt and decrypt messages. Ciphers have two different ways of processing a message:
1. Stream ciphers: work on one character of the message at a time. They perform their action on a single character or single bit and then move on to the next character or bit.
2. Block ciphers: work on chunks of the message, known as blocks, at the same time. They might take 100 characters of a message, for example, and encrypt them all at the same time.
Cipher Building Blocks
Cipher use 2 main building blocks:
1. Substitution ciphers: these actually change the characters in a message. A simple substitution cipher might, for example, shift all the letters in the message by two positions changing the As to Cs, the Bs to Ds, and so on. When someone wants to decrypt this message, they simply shift the characters back by two positions. This type of simple substitution cipher is also known as a rotation cipher because it simply rotates the alphabet several positions to the left or right.
2. Transposition ciphers: these don’t change the characters in a message, but instead they rearrange them. They’re basically scrambling up the message in a way that only someone who knows the decryption key can unscramble them.
5. Cryptographic Math
You won’t find complex mathematical questions on the exam, but you should be familiar with some of the basic terms and concepts that support cryptography.
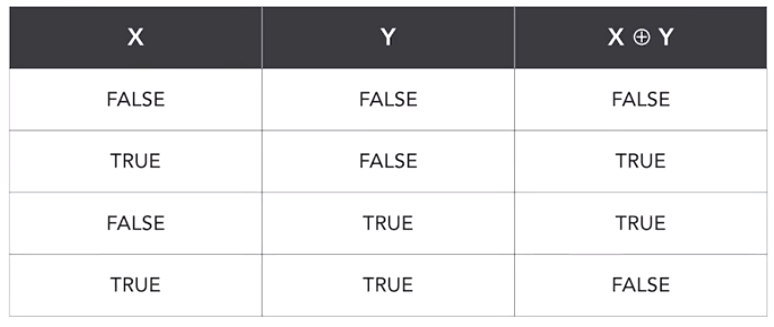
Exclusive Or (XOR)
Many cryptographic algorithms use the exclusive Or operation to combine plain text and cipher text with cryptographic keys. The exclusive Or operation is a logical operation that is true when one and only one of the inputs is true.
Pseudorandom Numbers
Pseudorandom number generators use a complex series of inputs and mathematical functions to produce numbers that are very close to random for use in cryptographic applications.
Properties of Ciphers
1. Confusion: in this a cipher must hide the connection between the cipher text and the key to make it more difficult to crack. In technical terms, every bit of the cipher text must depend upon more than one bit of the encryption key.
2. Diffusion: says that changing a single bit of the plain text should produce a change that is spread across a large portion of the cipher text. Ideally, changing one bit of the plain text would change half of the bits of the cipher text.
3. Obfuscation: is an application of cryptography in the world of software development. Software developers who wish to hide their source code from users may use cryptography to obfuscate their code, allowing users to run the code, but not allowing them to view the code itself.
6. The Perfect Encryption Algorithm
The one-time pad, invented by a telegraph expert in 1882, is an example of an unbreakable cipher. Using the one-time pad is fairly straightforward. It requires the use of a one-time pre-shared key the same size as, or longer than, the message being sent. In this technique, a plaintext is paired with a random secret key (also referred to as a one-time pad). Then, each bit or character of the plaintext is encrypted by combining it with the corresponding bit or character from the pad using modular addition.
The resulting ciphertext will be impossible to decrypt or break if the following four conditions are met:
- The key must be truly random
- The key must be at least as long as the plaintext
- The key must never be reused in whole or in part
- The key must be kept completely secret.
EG:
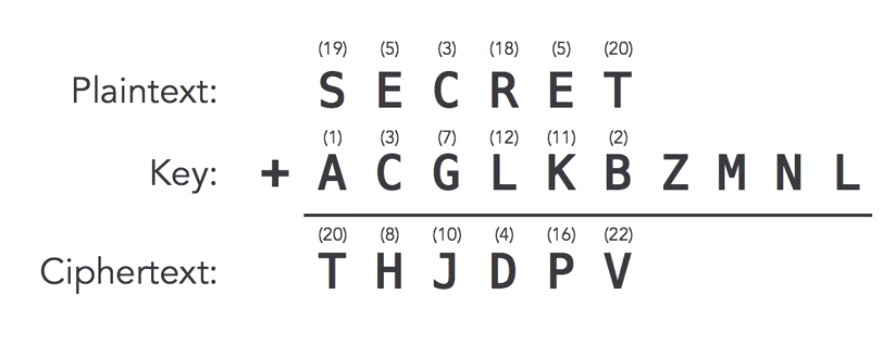
So if we have this perfect encryption algorithm that we’ve known about for more than a century, why aren’t people using it widely today? Well, because it’s very difficult to distribute one-time pads.
7. Choosing an Encryption Algorithm
EXAM TIP: do not try and build your own encryption algorithm unless you really know what you are doing!
Similarly, if a vendor claims that their software is secured with a proprietary encryption algorithm, and they won’t share the details, view that claim with the scepticism that it deserves. That’s a big red flag.
Security through obscurity: this means that the security of the algorithm comes from the fact that nobody knows how it works. Security through obscurity is a slanderous term and not something that you’d want to hear used to describe your own approach to security.
Choosing an algorithm
You should choose an encryption algorithm that is proven to be secure. The details of encryption algorithms are normally published and open for inspection by the security community. This public vetting process is important because it allows mathematicians and cryptographers to review the details of the algorithm, ensure that it is well-designed, and ensure that it is free of backdoors that might allow unintended access to information.
Choosing your key length
When you choose an encryption algorithm, you may also be able to select the length of your encryption key. Not all algorithms allow this as some have fixed-length keys. But if you are able to choose your key length, the longer your key, the more secure your information will be.
There is a downside, however. As keys get longer, the performance of the algorithm goes down. You’re trading off security for speed and making a classic decision that must balance security constraints with available resources.
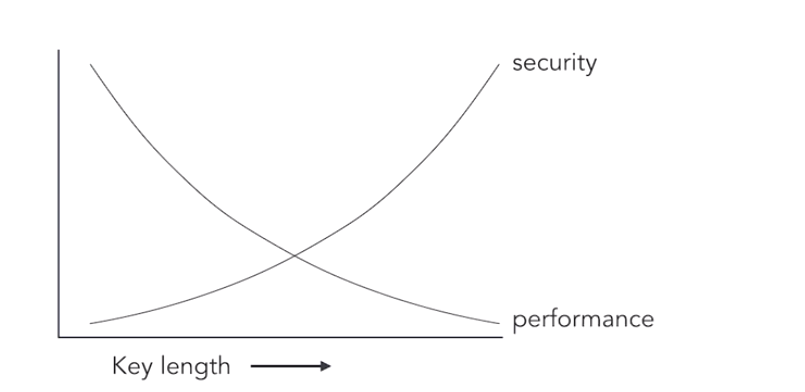
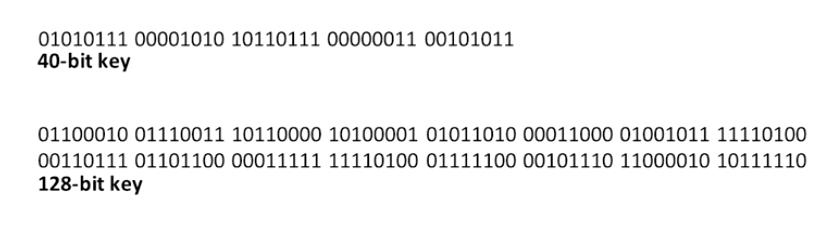
With the 40 bit key there are over one trillion possible combinations for this key. That may sound like a lot but it’s possible for a computer to break this key. If we bump encryption up to a 128-bit key, there are enough possibilities here that it wouldn’t be feasible to guess the key with a modern computer.
Implementing the chosen algorithm
As with algorithm selection, it’s best to adopt an implementation of your selected algorithm that is already proven. There are many development libraries and modules and cryptographic service providers available that have already implemented algorithms successfully, so you’d be well-advised to use tested and supported code rather than trying to write your own.
8. The Cryptographic Lifecycle
As cryptographic algorithms age, they often become insecure, either because researchers discover flaws in their implementation or because the key length used by the algorithm becomes vulnerable to brute force attacks. Therefore, it is important to have a lifecycle approach to cryptography that phases algorithms out as they become insecure.
NIST’s 5 Stage Cryptographic Lifecycle
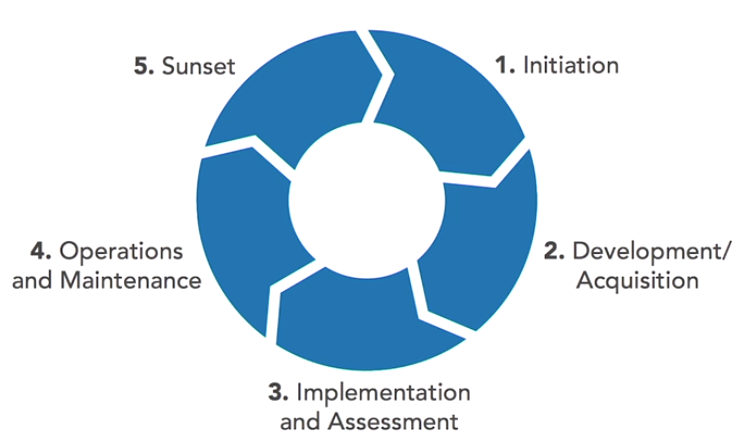
1. Initiation: During this phase, the organisation is looking for a new cryptographic system and gathers the requirements for that system. This should include the specific confidentiality, integrity, and availability objectives of the organisation based upon the sensitivity of the information that will be protected.
2. Development/Acquisition: The organisation finds an appropriate combination of software, hardware, algorithms, and keys that meets their security objectives.
3. Implementation and Assessment: this is where they configure the system for use and assess whether it properly meets the organisation’s security objectives.
4. Operations and maintenance: During this phase, the organisation ensures the continued secure operation of the cryptographic system.
5. Sunset: When the system is no longer viable for continued long-term use, the organisation transitions into phase five, Sunset. During this last phase, the organisation stops use of the system and destroys or archives sensitive material such as the keys used with the system.
