Contents
- Configuring Custom SaaS Enterprise Apps with Token Customisation
- Integrating On-Premise Apps by Using Azure AD Application Proxy
- Publishing Enterprise Apps in Azure AD
- Implementing and Configuring Consent Settings
- Monitoring & Auditing Access / Sign-ins to Azure AD Integrated Enterprise Apps
- Discovering Apps by using MCAS or ADFS reporting
Configuring Custom SaaS Enterprise Apps with Token Customisation
An example of this is:
- An app that runs on an onsite managed web server in the DMZ with an internet facing interface. EG: app1.spk.com
- We want to tie this to Azure AD for authentication so users go to Azure AD to get a token to access the app
- Azure AD has a service called “App Registrations” for this.
Configuring App Registrations
- Go to Azure AD -> App Registrations
- Click on the plus sign to create a new registrations
- Give it a name
- Who can access this?
— Accounts in this Azure AD tenant only
— Accounts in any Azure AD tenant
— Accounts in any Azure AD tenant and personal Microsoft accounts (skype, Xbox etc…)
— Personal Microsoft accounts only - Redirect URI: if you don’t want it to go directly back to the web app you can redirect it to a different page
- Click on Register
A web developer then needs to configure it on the web server side
Integrating On-Premise Apps by Using Azure AD Application Proxy
What is application proxy?
This is a feature of Azure AD that enables users to access on premises web applications from a remote client. This feature includes:
- Application proxy service: this runs in the cloud
- Application Proxy Connector: this runs on an on premise server
These work together to securely pass user sign on token from Azure AD to the web application
Features:
- Provides secure remote access to on-premise web applications
- Afters a SSO to Azure AD, users can access both cloud and on premise apps through an external URL or internal app
- Can provide remote access to RDP, Share Point, Teams and Line of Business Applications
Benefits:
- Simple to use: users can access your on premise apps the same way they access O365 apps
- Secure: On premise apps can use Azures authorisation controls and security analytics. Application proxy doesn’t require you to open inbound connections through your firewall
- Cost effective: On premise solutions typically require DMZs, edge servers, etc…
Basically, you can setup a web server on your internal network and not have to open a bunch of ports like 80 and 443. The onsite server has an agent that communicates with Azure AD. Users can still access it remotely as Azure is the middle man that manages the connection between them.
Application Proxy works with:
- Web apps that use Integrated Windows Authentication
- Web apps that user form based or header-based access
- Web APIs that you want to expose to rich applications on different devices
- Rich client apps that are integrated with the Microsoft Authentication Library (MSAL)
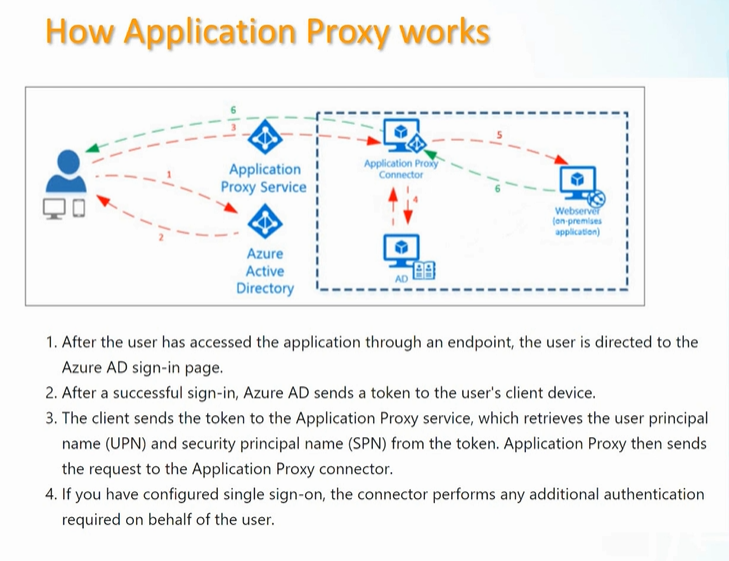
Components of users the Application Proxy
- Endpoint: this is a URL or user portal
- Azure AD: performs the authentication
- Application Proxy Service: runs in the cloud as part of Azure AD. Passes the sign on token from the user to the Application Proxy Connector
- Application Proxy Connector: lightweight agent that runs on Windows server inside your network. This communicates with the Application Proxy Service
- Active Directory: when SSO is configured the connector comminates directly with AD to perform any additional authentication required
- On premise web app: the app the user is trying to access
Publishing Enterprise Apps in Azure AD
Install the “Application Proxy Connector” agent on your web server
- Go to Azure AD -> Application Proxy
- From here you can download the “Application Proxy Connector” agent
- install this on your web server
Setup the App in Azure AD
You do this using the “Configuring App Registrations” instructions which we covered above.
Once the app is registered:
- Go to Enterprise Applications – > Your app
- Form here you can assign which users can access it, conditional access etc…
- Go to “Application Proxy”. This is where you tie the app to your on premise agent.
- Internal URL: this is a URL you will receive when you install the agent
- External URL: the public URL for your app
- Pre Authentication: use Azure AD or Pass through to your on prem domain controller
Implementing and Configuring Consent Settings
Sometimes a 3rd party application can request access to your organisations data. It asks the user to allow this access. Azure administrators can specify if they allow the user to grant this access or not.
- Portal to Azure AD -> Enterprise Applications -> Consent and Permissions. From here you can see the line: “When a user grants consent to an application, the user can sign in and the application may be granted access to the organisations data”
- User consent for application:
– Do not allow (an administrator will be required for all apps)
– Allow user consent for verified publishers, for selected permissions (Recommended).
if you select this option you are given other options where you can select the apps and permissions to grant
– Allow user consent for apps (users can consent for any apps to the organisations data) - Group owner consent or apps accessing data (Whether group owners are allowed to consent for application to access your orgs data for the groups they own)
– Do not allow group owner consent
– Allow group owner consent for selected group owners. Then you get to select the groups
– allow group owner consent for all groups
Monitoring & Auditing Access / Sign-ins to Azure AD Integrated Enterprise Apps
Checking Sign ins:
- Portal to Azure AD -> Enterprise Applications -> Sign in Logs
- Here you can see the user sign in logs and search, filter etc…
Usage and Insights
- Portal to Azure AD -> Enterprise Applications -> Usage and insights
- This gives insight into successful/failed logins for specific apps
Audit logs
- Portal to Azure AD -> Enterprise Applications -> Audit Logs
- This shows you everything involving different applications (updating info, add apps, granting permissions etc…)
With all these logs you can export them to CSV or JSON files
Discovering Apps by using MCAS or ADFS reporting
AD FS logs
- Portal to Azure AD -> Enterprise Applications -> Usage and Insights -> AD FS app activity
- Here you can look at the logs for any apps that are using AD FS for authentication
Cloud App Security portal
You need licences for this. This can discover information on a lot of different cloud apps. At the time this video came out it was over 23,000…
It gives you a security and compliance score for different apps. And tells you why it got that score.
This is a handy tool for investigating apps your company may want to use.
