Contents
2.2.1 Routers, Switches and Bridges
Routers,switches and bridges are the building blocks of networks
Switches
A switch is hardware device on a network that connects devices on a network by using packet switching to receive and forward packets to its destination. Switches generally use MAC addresses to forward data at the Data Link layer (Layer 2). Some switches can forward data at the Network Layer (Layer 3).
Routers
Routers connect networks together. They make decisions about the best path for traffic to follow to its final destination. Routers also perform some security functions using ACL’s (Access Control Lists) to limit the traffic that may enter or leave a network based upon the organisations security policies. Routers operate at Layer 3.
Bridges
These are layer 2 devices that connect two networks together.
Media Gateways
https://www.metaswitch.com/knowledge-center/reference/what-is-a-media-gateway
A media gateway is a device used in the core network of a telecom network operator to provide transformation and interworking between media streams that use different network standards, communication protocols, codecs and physical connections, so that phone calls work properly between networks using different technologies.
2.2.2 Firewalls
These are the security guards of the network. They analyse all the attempts to connect to systems on the network and determine whether those requests should be allowed or denied according to the organisations security policy. Firewalls generally sit at the perimeter of the network between the router and the internet.
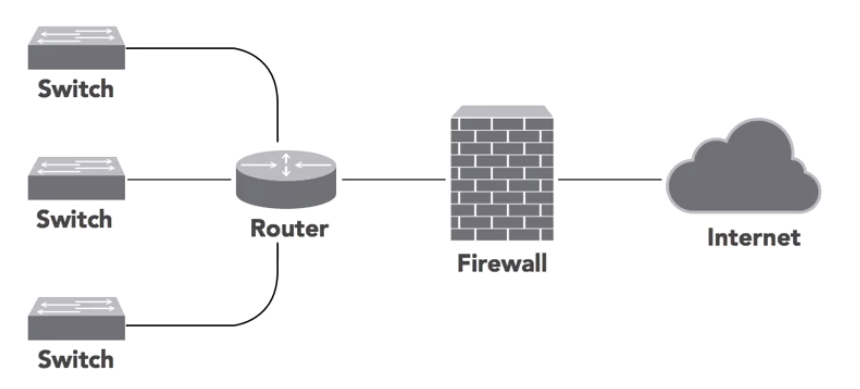
DMZ (Demilitarised Zone)
This is a small private network sitting between the internet and the organisations private network. The organisations external facing services can sit in the DMZ. this adds an extra layer of scurity to the network as only what is in the DMZ can be accessed from external. This allows the organisation extra time to identify and detect breaches before they penetrate the private network. They can also be known as Perimeter Networks or Screened Subnets.
Services that sit in the DMZ include:
- web servers
- mail servers
- FTP servers
- VOIP servers
Stateful Inspection
Firewalls use a technique known as stateful inspection that allows them to keep track of established connections. EG: when a user on the internal network requests a web page from a server, the firewall notes that request and allows the web server to respond and the two systems communicate back and forth for the duration of the connection without reevaluating the request each time a new packet appears at the firewall.
Firewall Rules
Firewall rules contain the following:
- Source system address
- Destination system address
- Destination port and protocol
- Action (allow or deny)
2.2.3 Proxies
These server as intermediaries that prevent users from connecting directly to web servers.
The proxy server sits between the user and the internet. The user connects to the proxy server, the proxy
server connects to the web servers. All traffic passes through the proxy.
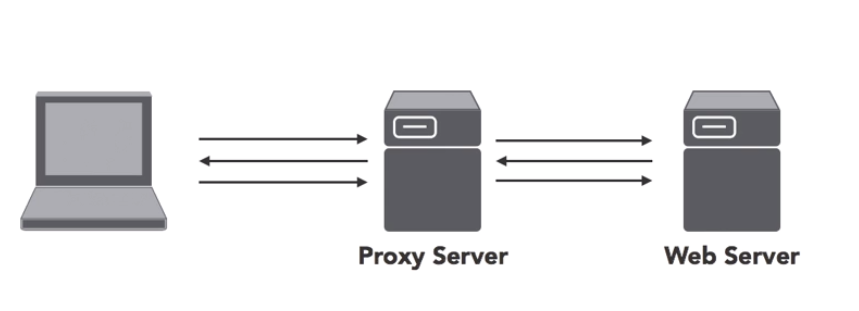
This has 3 important benefits:
- Anonymity: the web server never sees the IP address of the user, it only sees the IP of the proxy server
- Performance boosting: the proxy server uses caching by storing copies of frequently accessed websites and serves these to users, reducing the network bandwidth
- Content filtering: it can perform security tasks to ensure users aren’t visiting malicious websites or sites they shouldn’t be accessing.
Forward Proxies work on behalf of the clients
Reverse proxies work on the servers behalf. This sits in between the web server and the internet and all traffic to the web server passes through it.
Transparent Proxies work without the client or servers knowledge. Also known as inline proxies or forces proxies. They sit on the clients network and intercepts requests for web services on their behalf.
2.2.4 Load Balancers
These help web servers scale by distributing the workload among multiple servers (Balancing the load).
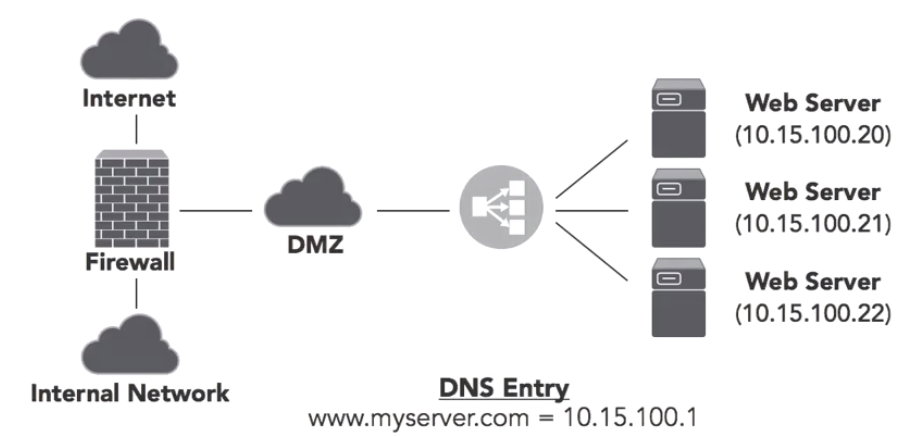
In the sample picture the DNS entry points to the IP of the load balancer instead of directly to a web server.
Load Balancers can also fill some security roles:
- SSL certificate management
- URL filtering
- Limiting access to certain IP ranges
- Limiting access to certain parts of the website
Methods of Load Balancing
Round Robin Scheduling: this is the simplest method. The load balancer rotates through the web servers giving each one its equal share of traffic. But this may not be the most efficient. If one server is more powerful it may be able to handle more requests. Or one server might get an intense request that requires lots of resources, then it may not be able to handle any more requests for sometime.
Advanced scheduling algorithms choose servers based upon performance and capacity.
Session Persistence: some applications may require that the users return to the same web server to maintain session persistence. In these cases the user may be assigned a web server using the load balancer scheduling algorithm.
Single Point of Failure
Load balancers can be a single point of failure in a network, so you need to make sure they run in a high availability mode in one of the following topologies-
Active-Active: the two load balancers run side by side and each handles a portion of inbound traffic to the web servers. If one goes down the other load balancer handles all the requests. this means it is still operating but with diminished capacity.
Active-Passive: In this approach one load balancer handles all the requests while the other sets and monitors the connections. If the active load balancer goes down, the passive load balancer immediately takes over and handles all of the requests. In this method you have no loss of capacity during a failure, but the passive load balancer sits there most of the time not doing much.
2.2.5 VPNs and VPN Connectors
A virtual private network extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network.
VPN’s work by using encryption to create a tunnel between two systems over the internet. If an attacker gains access to traffic between these two secure points all they see is encrypted traffic.
Types of VPN’s
- Site-to-site VPN: this allows the interconnection of remote networks, such as branch offices to the head office. Another example of this is 2 school campuses in different geographical locations that are connected and operate as if they are one big campus
- End User VPN: this allows mobile workers to securely connect form remote locations to the organisations network.
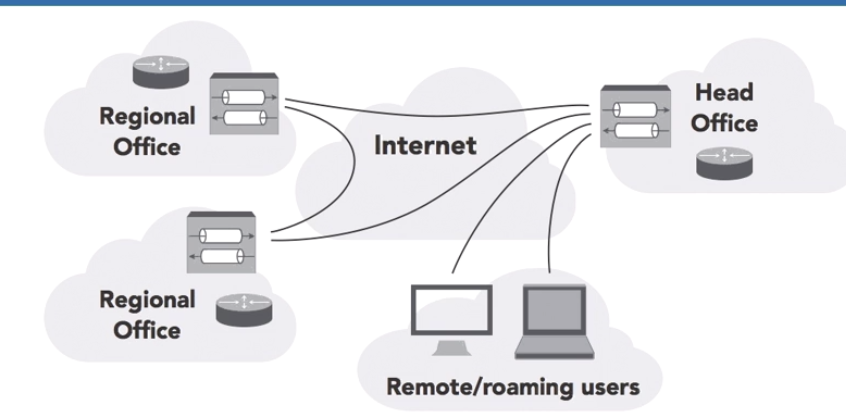
VPN Endpoints
VPN’s require an endpoint on the network that accepts VPN connections. Many different devices may serve as VPN endpoints:
- Firewalls
- Routers
- Servers
- Dedicated VPN Concentrators – these are used when there are high volumes of VPN use as these devices are very efficient at VPN connections and can manage high bandwidth traffic with ease.
VPN Protocols
IPSec (Internet Protocol Security)
- works at the network layer
- provides robust and secure transport can be difficult to configure
- often blocked through firewalls
- often used for site to site VPN’s
SSL/TLS
- application layer VPN
- easier to configure
- often used for remote access VPN’s
- works on any system with a browser
- uses port 443 for communication. This is typically allowed through firewalls.
Tunnelling Approaches
- Full Tunnel VPN: All network traffic from the connected devices is routed through the VPN tunnel. This includes all web traffic.
- Spilt Tunnel VPN: Only traffic destined for the organisations network is sent through the VPN tunnel. Other traffic is routed directly from the device to the internet. Split tunnels may give a false sense of secuirity as users might think that all of their traffic is being sent securely, but some of it is going to the internet and may not be secure.
Always On VPN
In this the mobile device automatically connects to the organisations VPN when they are powered on. This ensures all traffic from the device is always securely communicated.
2.2.6 IPSec (Internet Protocol Security)
When the TCP/IP protocol suite was created in the 70’s, they didn’t pay too much attention to security as is it wasn’t an issue at the time. We now need to retrofit them to add on security capabilities.
The IPSec framework is a set of protocols to add security capabilities to TCP/IP networking. IPSec goes deep into the protocol stack and provides security for the entire payload of encrypted communications.
IPSec Protocols
- ESP (Encapsulating Security Payload): this provides confidentiality and integrity protection for packet payloads.
- AH (Authentication Headers): this uses an integrity check to provide tamper proofing for IP packets. It ensures that no changes are made to the header of the packet while it is in transit over the network.
A single communication may combine both ESP and AH
Security Associations (SA’s)
Each system participating in IPSec makes available a list of cryptographic protocols and hash functions that it supports. A cryptographic protocol and hash function together is known as a Security Association. Systems that wish to communicate with each other compare their list of Security Associations to find the strongest SA they have in common.
IPSec VPN Types
- Site-to-Site VPN: traffic between two sites travels through the encrypted IPSec tunnel which protects he traffic over a public network. This is known as tunnel mode.
- End users VPN: the end user uses IPSec VPN client to connect individual computers to a remote network. This is known as transport mode.
IPSec VPN’s were very common but have now fallen out of flavour due to the complexity of setup. TLS VPN’s are easier to configure.
2.2.7 Network Intrusion Detection and Prevention
Intrusion Detection Systems (IDS)
An IDS sits on the network monitoring traffic, looking for signs of potential malicious activity. They look for things like:
- SQL injection attacks
- Malformed packets that may be trying a DDoS attack
- Unusual logins
- A client on the internal network that may be trying to contact a botnet command and control server
IDS alert administrators of the malicious activity. But the administrator may not be able to immediately review the situation, or they may be overwhelmed with the volume of alerts. This is where Intrusion Prevention Systems come into play.
Intrusion Prevention Systems (IPS)
The IPS attempts block suspicious activity when it sees a threat. In most cases it this means blocking the malicious traffic from entering the network.
IDS/IPS Errors
False Positive Errors: the system triggers an alert when an attack did not actually take place
False Negative Errors: an attack did take place but the system failed to report it
Methods of Detection
Signature Detection Systems
This is similar o how a lot of Anti Virus systems work:
- The systems contains a database with rules describing malicious activity
- Once the system matches some traffic activity with the rules in its database, it takes some action
The downside of this method is that it fails to detect brand new attacks, as it wont know about them yet. the upside is these systems work very well with a low false positive rate.
Anomaly Detection Systems
This method builds a modal of “normal: activity, then sends an alert to any deviations to this activity.
EG: the system might notice that a user who normally connects to VPN during the early evening hours from Melbourne, may now be connecting in the middle of the night from Russia. The system can then send an alert and may also block the connection depending on the policy.
The models developed by these systems are often application aware and understand how to dissect the layer 7 protocols. Anomaly detection does have the potential to notice new attacks but it has a high false positive error rate, and it is not widely used by administrators.
EXAM TIP: Anomaly detection, behaviour based detection and heuristic detection are the same thing!
IPS Deployment Modes
- In-band (inline) deployments: the device sits in the path of network communications and all internal/external traffic must pass through it. The device can block suspicious activity from entering the network. While this approach allows an active response, it also adds the risk that an issue with the IPS can disrupt all network communications.
- Out-of-band (passive) deployments: this is not in the network path but it sits outside the flow of traffic. It is connected to a SPAN port (Switch Port Analyser, or port mirroring) on a switch which allows it to receive copies of all traffic sent through the network. It scans this traffic but cannot disrupt it before it reaches its destination. It is called passive because it cannot block the initial attack, but it can prevent future attacks by sending commands to block future traffic form offending systems.
2.2.8 Unified Threat Management (UTM)
Purchasing all these different security devices can be expensive. UTM solutions address this by putting all the security functions on a single device.
Basic UTM Functions:
- Protecting network against attacks
- Blocking unsolicited traffic
- Routing traffic to and from the internet
Additional Security features:
- VPN connectivity
- IDS
- IPS
Small Business Features:
- URL filtering
- Content inspection – remove malicious web content returned by otherwise trusted servers
- Malware inspection – works like Anti Virus for network and web traffic
- Email and spam filtering
2.2.9 Oauth & OpenID Connect
These protocols provide a federated Single Sign-On experience for the web. Some providers include: LinkedIn, google, Facebook, and Amazon
Authentication: This means confirming your identity
Authorisation: this means being allowed access to the system, or certain parts of the system
Oauth
this is an autorisation protocol designed to work across a variety of web services. It doesn’t provide authentication itself.
OpenID Connect
This is an identification and authentication protocol designed to work with Oauth.
