Contents
2.11.1 TLS & SSL
Digital certificates allow for the secure exchange of public keys over otherwise untrusted networks.
Types of encryption
Symmetric Encryption: The same key is used for encryption and decryption. The issue with this method is that the key must shared to with the sender and receiver.
Asymmetric Encryption (Public key): The recipient generates two keys. The public key, which it sends to the sender to encrypt the data, and the private key which the recipient uses to decrypt the data. This is the most common method.
Transport Layer Security (TLS)
This uses certificates to facilitate secure communication over public networks.
TLS process between two systems:
- The client sends a request to the server asking the server to initiate a secure session. This request includes the list of cipher suites supported by the client. This is a laundry list of encryption algoruthms and hash functions that the client understands.
- The server compares this list with its own list of algorithms. Once the server finds a match it sends back 2 pieces of information-
a) the cipher suite it would like to use (EG: SHA-256 with RSA)
b) the servers digital certificate which contains the servers public encryption key - The client check what certificate authority (CA) issued the certificate and uses the CA’s public key to verify the digital signature on the certificate. It also verifies that the server name on the certificate matches the DNS name of the server and that the certificate has not been expired or revoked.
- Once the client is satisfied about the servers identity, the client creates a random encryption key called the session key. This is a symmetric encryption key that will be used for this one communication session between the client and the server. The client uses the servers public key to encrypt the session key and sends it to the server.
- The server uses its private encryption key to decrypt this
- The two systems can then communicate for as long as they like using the session key
- Once they close the connection the session key is destroyed. IF they want to communicate again the TLS handshake happens all over again.
EXAM TIP: it is important to remember that TLS is a protocol that applies encryption algorithms, but it is not an encryption algorithm itself. You can’t encrypt something with TLS
EXAM TIP: session keys are also known as ephemeral keys
Secure Sockets Layer (SSL)
This is the predecessor to TLS and is now considered insecure. There are known security flaws with it and it should no longer be used.
2.11.2 Protocol Security Use Cases
The following are examples of how to secure commonly used protocols.
Voice and Video
Voice and Video communications should use TLS encryption wherever possible.
RTP-(Real-time Transit Protocol) based VoIP services should use the secure SRTP (Secure Real Time Transit Protocol) protocol.
Network Time Protocol (NTP)
This syncrhonises the time on different systems. In the past vulnerabilities have NTP servers to be used in DDoS attacks.
NTPSec is the secure version of this protocol. It is open source.
Email Protocols
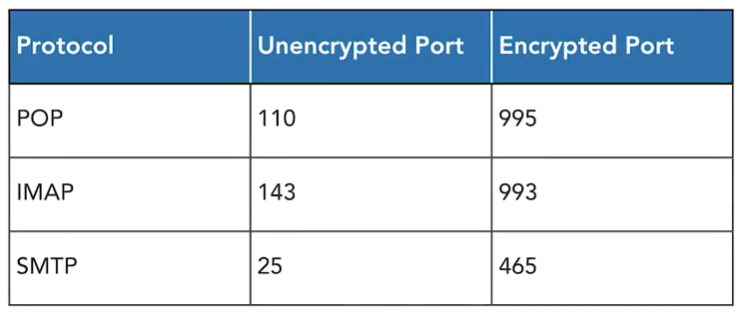
You can encrypt email messages and attachments at the application layer with the S/MIME protocol. This is a widely accepted protocol for sending digitally signed and encrypted messages. S/MIME allows you to encrypt emails and digitally sign them.
Secure Networking Protocols
- Use SSH instead of Telnet (telnet sends everything in plain text) for router and switch administration. SSH runs over TCP port 22 and uses public key cryptography to exchange an ephemeral session key in the same manner as TLS.
- Replace older versions of SNMP with SNMPv3
- Use DNNSEC to add digital signatures to DNS
- Limit authorised DHCP servers to eliminate rogue DHCP server on your network
- Use LDAPS as a secure alternative to LDAP
Secuing Common Protocols
Many common protocols that we rely upon today do not have built-in encryption and require modification to support encryption technology.
|
Unsecure |
Secure |
Notes |
|
HTTP |
HTTPS |
Adds TLS to web browsing |
|
FTP |
FTPS |
Adds TLS to FTP |
|
FTP |
SFTP |
Transgers files over SSH |
|
FTP |
SCP |
Secure Copy. This provides more secure command line transfer over SSH |
Exam TIP: the Trivial File Transfer Protocol (TFTP) is not secure and is rarely used.
2.11.3 Cryptographic Hardware
Cryptography requires a great deal of mathematical computation and there can be fairly slow. Engineers often make cryptography more efficient by building special purpose hardware that is designed specifically for encryption and decryption.
SSL/TLS Accelerators
The SSL/TLS handshake process can be complex and time consuming. This can be a bottle neck for webservers. SSL and TLS accelerators are special hardware designed specifically to complete this process. When a device begins the process it hands control over the accelerator, which then complete the handshake and returns control to the web server CPU for handling the remainder of the session
SSL/TLS Decryption
Encryption can make life difficult when trying to analyse traffic in the in case of an intrusion or malicious activity. SSL and TLS decryption technology allows organisations to view the encrypted communications that devices on their network take part in. They do this by effectively engaging in a man-in-the-middle attack against their own systems. The SSL/TLS decrypter presents a wildcard certificate to the client device that appears legitimate for any site on the internet. The client device is configured to trust this certificate, and opens a connection to the decrypter when then opens a legitimate SSL/TLS connection to the real destination.
The decrypter then receives all traffic from the client, decrypts and inspects it, then re-encrypts it for delivery to the final destination. When the remote server responds the decrypter follows the same process in reverse.
This technology is sometimes found in firewalls and other security appliances.
HSMs (Hardware Security Modules)
These special purpose computers manage encryption keys and perform cryptographic operations in a highly efficient manner. They can create and manage encryption keys without exposing them to any humans.
They are expensive but very effective.
